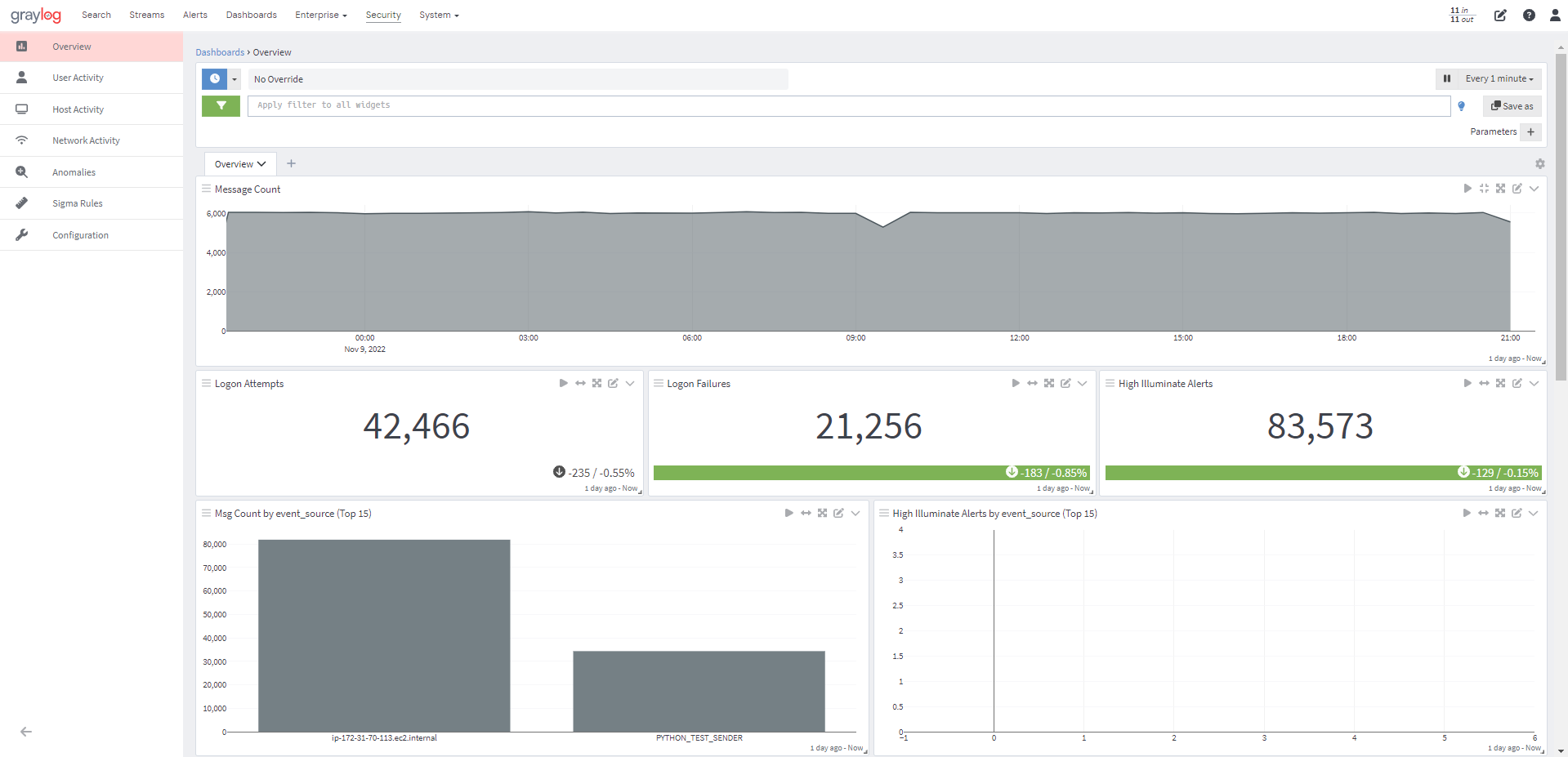
Alerting
Receive alerts via email, text, Slack, and more. Update alert criteria based on a dynamic list in a lookup table.
Functionality you need without the complexity and cost of traditional SIEM solutions.
Work as a team to keep your organization secure.
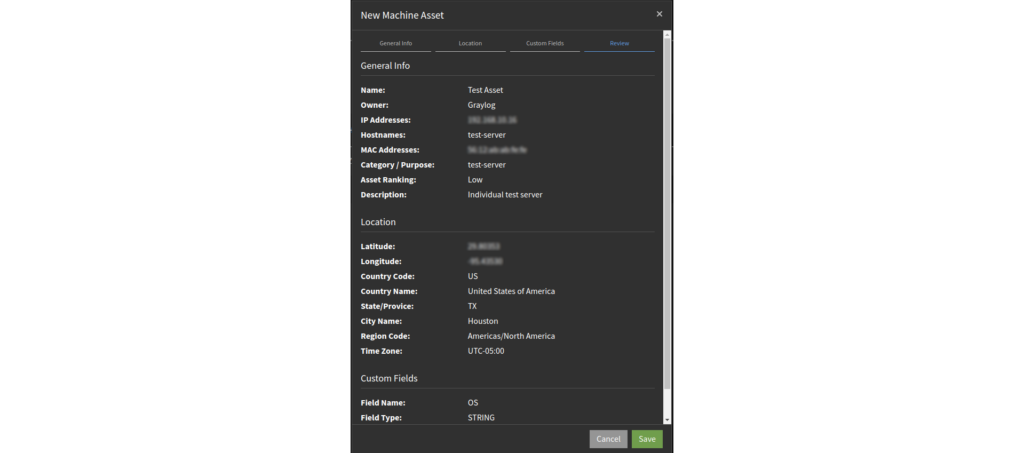
Track assets across your environment while enriching your log data
Stay on top of ever-changing regulatory compliance obligations.
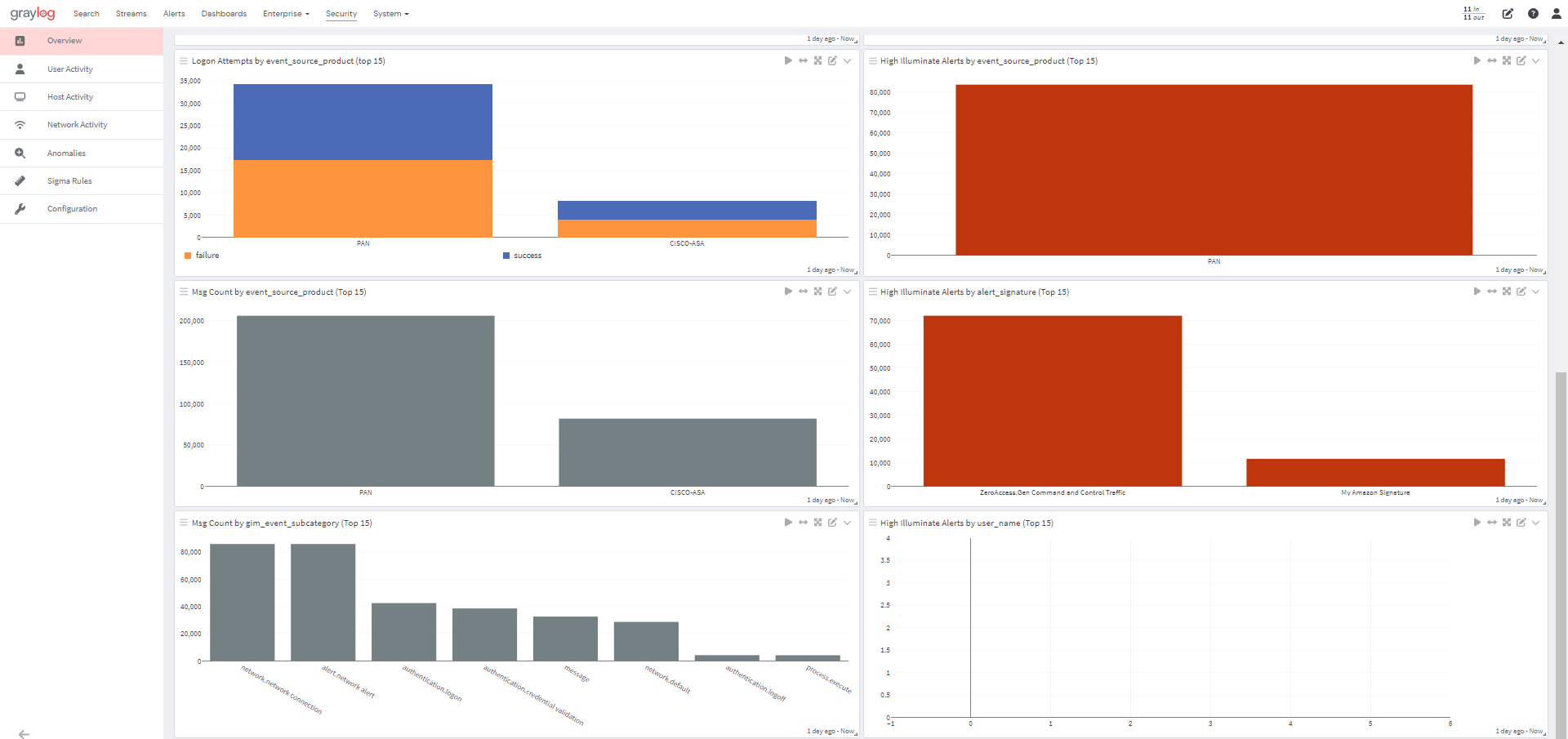
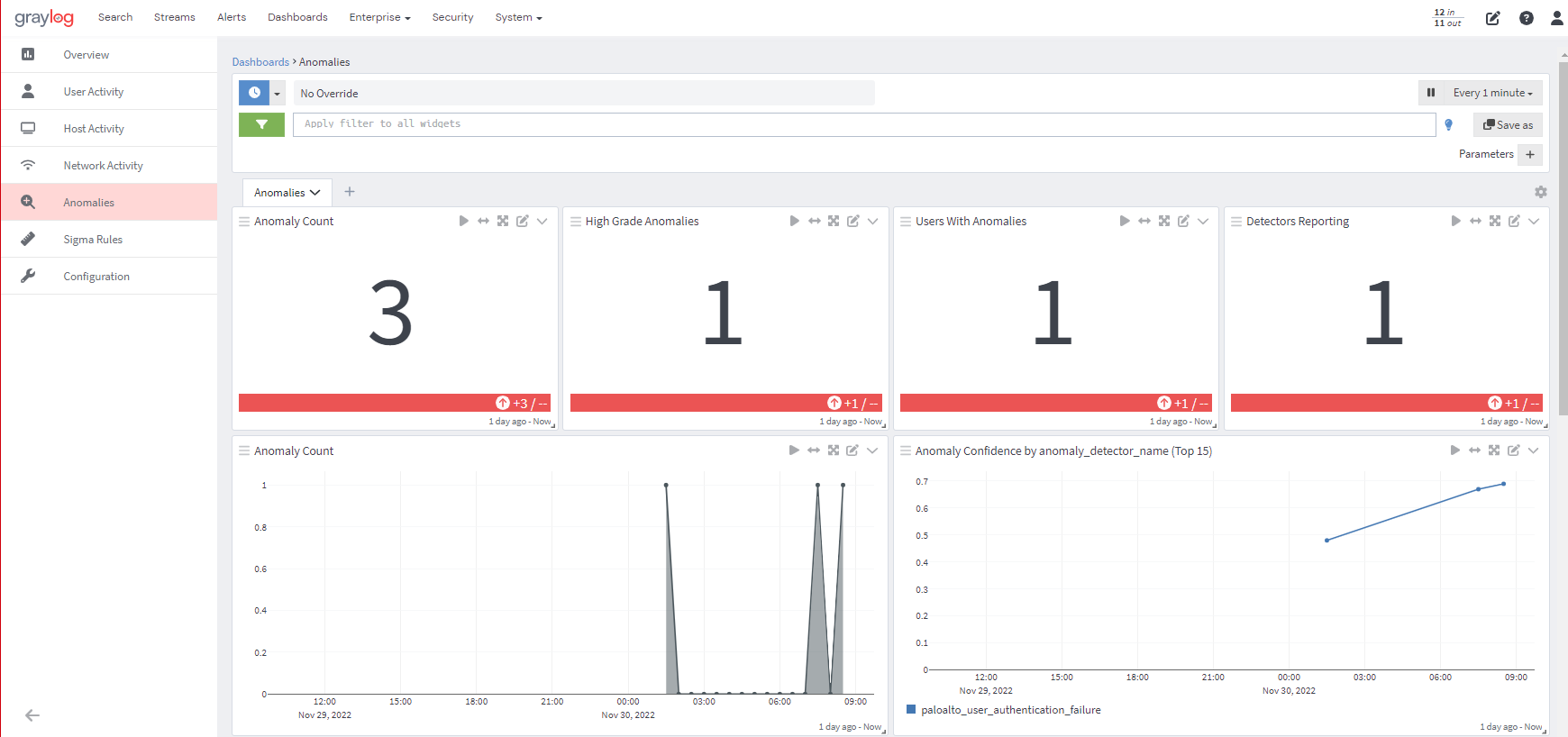
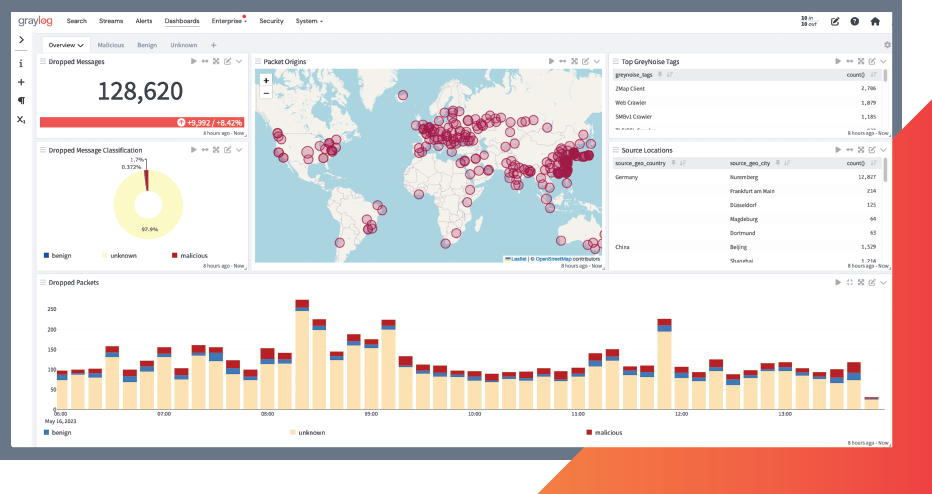
Proactively detect, hunt, and investigate internal and external threats.
Be the first to know when potential problems need attention.
Resource-constrained organizations need affordable and proactive threat detection, incident analysis, investigation, and response, and compliance reporting to strengthen their security posture. Graylog Security combines centralized log management, data enrichment and normalization, correlation, threat detection, incident investigation, anomaly detection, and reporting capabilities into a single solution that’s easy to deploy, manage, and use. We’ve designed our security platform to provide the functionality you need without the complexity and cost of traditional SIEM solutions.
Graylog Security’s cloud-native capabilities, intuitive UI, and out-of-the-box cybersecurity-focused content means you can start getting actionable insights from your logs quicker when compared to legacy SIEMs. Lower your labor costs with features designed to help significantly reduce alert fatigue, get you to the informed answers you need fast, and empower your security professionals.
Receive alerts via email, text, Slack, and more. Update alert criteria based on a dynamic list in a lookup table.
Capabilities that quickly learn "normal" behavior and automatically identify deviations for users and entities at scale, with continuous fine-tuning and improvement over time.
Store older data on slow storage and easily re-import it into Graylog when you need it.
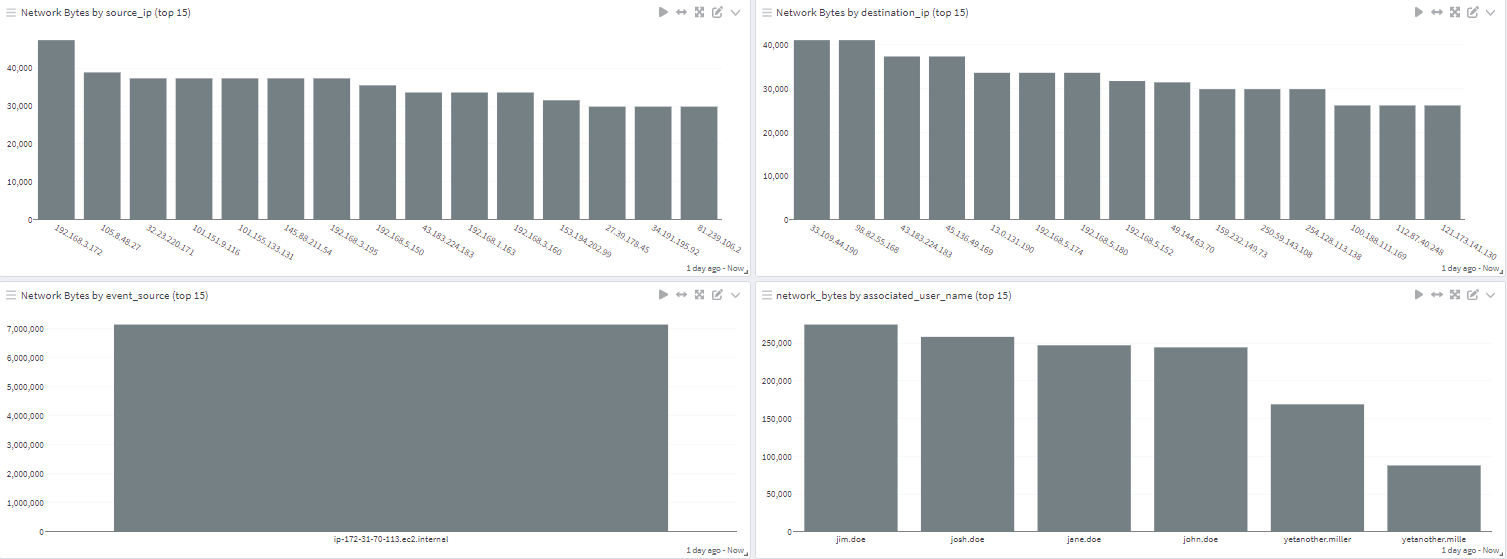
Gain insight across your environment with the ability to track different assets and enrich log messages with additional information.
Track who accessed what log data and what actions they took against it to ensure compliance and security.
Leverage Graylog’s dashboard functionality to easily build and configure scheduled reports.

Combine widgets to build customized data displays and automate the delivery of reports to your inbox.
Perform faster research by adding WHOIS, IP Geolocation, threat intelligence, or other structured

All-in-one workspace to collect and organize datasets, reports, evidence, and other context while investigating a potential incident.
Build and combine multiple searches for any type of analysis into one action and export results to a dashboard.
Start fast with prebuilt content — search templates, dashboards, correlated alerts, dynamic look-up tables, and more.
Combine widgets to build customized data displays and automate the delivery of reports to your inbox.
Easily share data with other business critical systems for full transparency and collaboration.
Add context to event log data with your existing threat intelligence feeds and pinpoint potential security issues.
"Best SIEM and log aggregation tool available right now. The amount of flexibility and insight into logs and operations provided by it are astounding."

At Graylog, we want you to get all your questions answered before you buy. Still undecided? Schedule your Graylog Security demo today and see our powerful log management platform in action.
Subscribe to the latest in log management, security, and all things Graylog Blog delivered to your inbox once a month.
Follow Us:
© 2024 Graylog, Inc. All rights reserved