Graylog Security
Graylog Security: The SIEM That Ends Trade-Offs
Protect your organization with complete visibility, faster threat detection, and predictable costs without compromise. Full visibility. Smarter detection. Faster investigations. Predictable costs. All without compromise.
81%
number of false positives out of 16,937 weekly cybersecurity alerts
(Ponemon Institute)
24 hrs
average Mean Time to Respond (MTTR) for cybersecurity incidents
(Armature Systems)
>200 days
time to identify a breach due to cost-driven log filtering
(OmniCyber Security )
Bringing SIEM Without Compromise to Life
Graylog Security is a modern SIEM platform built to remove the barriers that slow security teams. Every capability helps solve real operational challenges by reducing alert noise, accelerating investigations, lowering costs, and improving visibility. With Graylog Security, analysts can move faster, stay focused, and respond smarter without compromise.
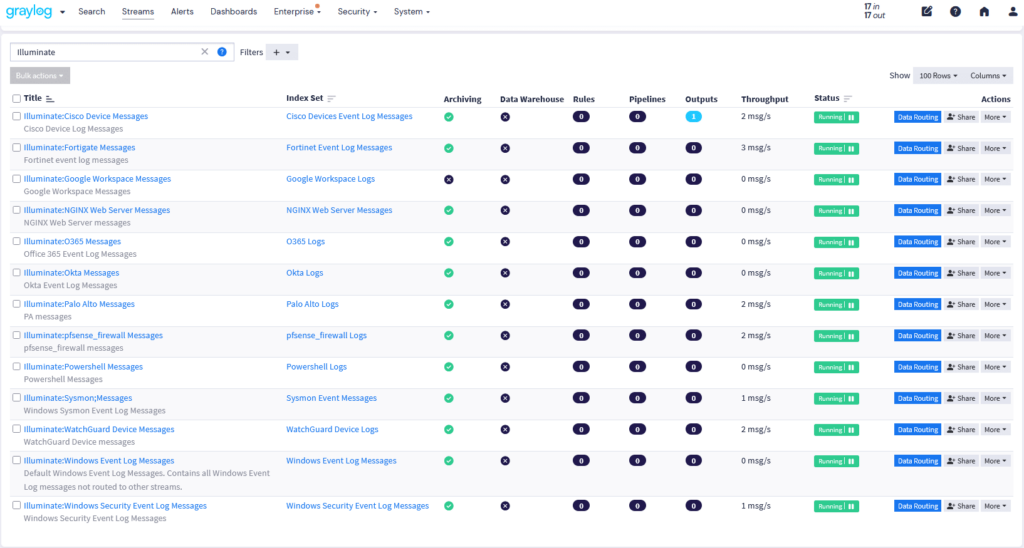
Log everything—pay only for what you use.
Traditional SIEMs force you to choose: retain data or control costs. Graylog Security shatters that model. Our built-in Data Lake and Selective Log Retrieval capabilities ensure you can keep the data that matters and access it instantly to add context to investigations while avoiding unpredictable charges. Why limit your logging? With Graylog Security, visibility scales with your needs—not your bill.
- Preview data before ingest
- Store years of logs affordably
- Retrieve exactly what you need—only when you need it
- Enhanced AWS Security Lake integration allows for direct preview, filtering, and retrieval of stored log data, accelerating investigations and reducing storage costs.
- A new Lake Retrievals Page improves visibility into archived data access, making retrieval management faster and more transparent.
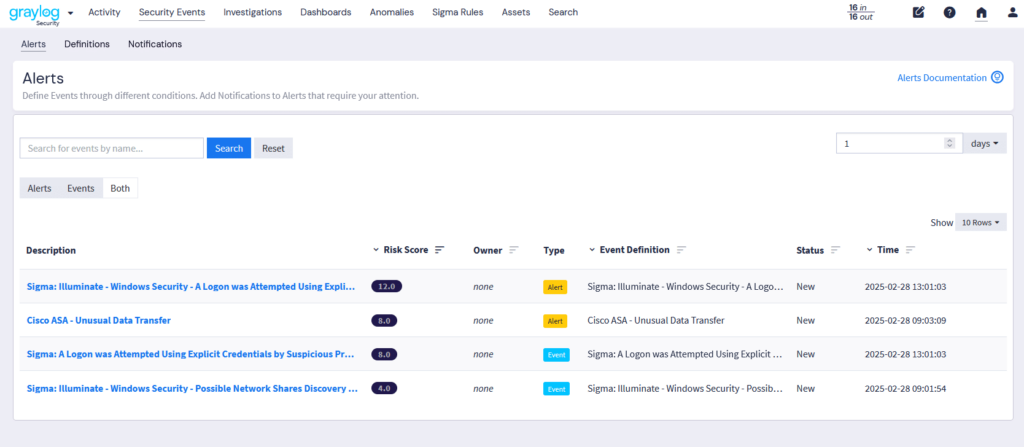
Cut through the noise. See what actually matters.
False positives are the enemy of effective security operations. Graylog Security’s contextual risk scoring, powered by Adversary Campaign Intelligence, amplifies real threats and suppresses the rest. From scattered events to full attack stories, Graylog Security shows you the bigger picture.
- Prioritize based on asset criticality
- Connect the dots between alerts
- Reduce alert fatigue with smarter triage
- Integrated AI features such as anomaly detection and risk scoring strengthen correlation accuracy and highlight emerging patterns before they escalate.
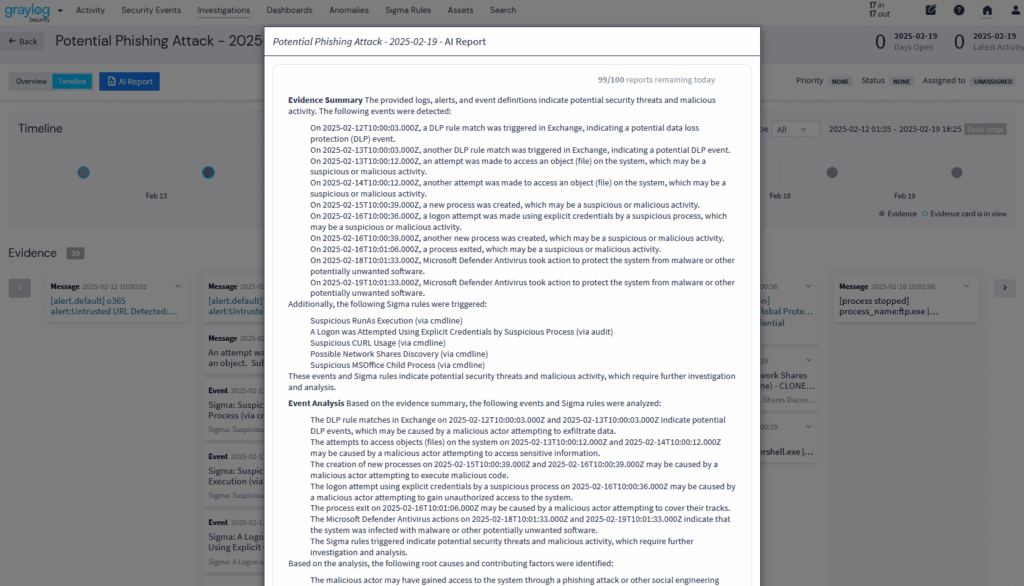
Automate the mundane. Accelerate the critical.
Why dig through logs manually when you can get answers in clicks? With Graylog Security’s Pivot-to-Search, Automated Workflows, and Prebuilt Content Hub, analysts can go from detection to response in minutes. No PhD required—Graylog Security makes every analyst an expert.
- Guided log source and content onboarding
- One-click pivoting across events
- Out-of-the-box detections with Sigma 2.0
- AI Summarization now explains dashboard or widget findings in plain language, helping analysts confirm trends and communicate results instantly.
- New Workflow Orchestration automates repetitive investigation steps and uses AI guidance to streamline triage and remediation.
- Investigation Summaries use built-in AI to compile findings, patterns, and recommendations in seconds, reducing documentation time.
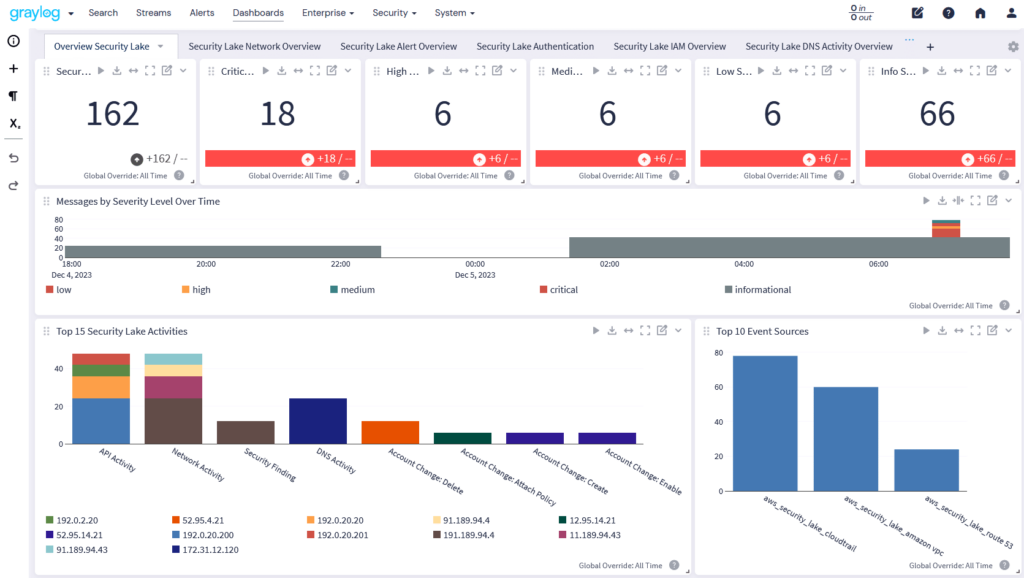
Cloud, on-prem, or hybrid—it’s your data, your rules.
Avoid vendor lock-in with Graylog Security’s flexible deployment model. Whether you’re cloud-native, data-center-anchored, or hybrid-driven, Graylog Security adapts to your environment seamlessly and securely.Graylog Security meets you where you are and scales as you grow.
- Same experience everywhere
- Easy MSSP multi-tenancy
- No forced SaaS limitations
- Integrate with MCP Services for secure, AI-driven configuration, analysis, and automation.
Integrated AI Assistance
What It Means:
Graylog Security delivers AI-powered capabilities across the platform, including anomaly detection, risk scoring, guided search, and automated investigation summaries. Additional features are currently in development.
Why It Matters:
Teams gain faster insights, smarter correlations, and improved decision support without relying on external AI tools or manual analysis.
No more data taxing. Just real ROI.
Unlike traditional SIEMs, Graylog Security aligns cost to value—not just ingestion. Archive all your data, activate what you need, and say goodbye to budget anxiety. Log fearlessly. Scale confidently. Graylog Security’s pricing puts you in control.
- Fixed, predictable pricing
- Value-based licensing
- Full retention, no surprise bills
Designed for Security Analysts, Built for CISOs, and Loved by Admins
Security Analyst
Cut through the noise. Investigate in clicks.
Security teams are overwhelmed by false positives and alert fatigue. With Graylog Security, you’ll surface real threats faster and reduce manual work with contextual scoring and automation.
What You’ll Love:
- Risk-Based Alerting: Elevate critical threats, suppress noise
- Campaign Mapping: See how alerts connect to full attack chains
- Click-to-Act Workflows: Investigate, pivot, and respond in seconds
- Prebuilt Content Hub: Skip rule writing and get started immediately
“With Graylog Security, we focus on threats—not our SIEM.” -Senior Security Analyst, Healthcare
SIEM Admin
Take control of your SIEM—without the complexity.
Are you tired of clunky interfaces and brittle configurations? Graylog Security makes onboarding, tuning, and scaling easy with intuitive tools and intelligent automation.
What You’ll Love:
- Input Setup Wizard: Fast, guided onboarding of log sources
- Sigma 2.0 & Content Hub: Build or import detections with ease
- Flexible Deployment: Run Graylog Security in the cloud, on-prem, or hybrid
- Selective Restore: Manage hot vs. cold data with precision
“We deployed Graylog in hours, not weeks—and got visibility right away.” -SIEM Admin, Public Sector
CISO
Security that scales with you—not against you.
CISOs need visibility, risk context, and control over costs. Graylog Security delivers intelligent threat detection and long-term visibility without unpredictable licensing.
What You’ll Love:
- Adversary Campaign Intelligence: See who’s targeting you and how
- Threat Coverage Analyzer: Align detection coverage to business risk
- Transparent Pricing: No per-GB penalties, just outcome-based value
- Data Lake Preview & Selective Restore: Full visibility, smarter cost control
“Graylog gives us the insights we need—with budget predictability we can trust.” –CISO, Banking & Finance
MSSP
Deliver improved detection & response—at scale.
MSSPs need a platform that’s flexible, cost-efficient, and fast to operationalize across clients. Graylog Security gives you scalable, multi-tenant capabilities with automation and pricing that work.
What You’ll Love:
- Cloud-Ready Multi-Tenancy: Serve multiple clients securely
- Automated Workflows: Reduce MTTR and maximize analyst efficiency
- Predictable Licensing: Scale services without exploding costs
- Selective Retrieval: Cut costs for long-term retention clients
“Graylog helps us deliver premium MDR at an efficient margin.” -MSSP SOC Manager
The Future of SIEM Is No Compromise
Security teams deserve better than slow investigations, limited visibility, and unpredictable costs. With Graylog Security, you get a platform built to work with you, not against you. Whether you’re streamlining threat response, scaling operations, or demonstrating compliance, Graylog Security delivers the intelligence, automation, and flexibility your team needs to stay ahead of modern threats.