We know that Graylog is just one piece of your security puzzle. That’s why we offer out-of-the-box integrations with industry-leading platforms, including:
Be Operational In Minutes.
Expert-built parsers, dashboards, and alerts that accelerate detection across cloud, endpoint, and network sources. Graylog Illuminate content gives your team a head start. With out-of-the-box content packs for AWS, Microsoft 365, Palo Alto Networks, and dozens more, you can centralize logs, normalize data, and surface threats—without custom development. From the moment data starts flowing, Illuminate provides parsers, dashboards, and detection rules that help analysts zero in on critical activity: catching real threats, not configuring fields.
We know that Graylog is just one piece of your security puzzle. That’s why we offer out-of-the-box integrations with industry-leading platforms, including:
Get logs flowing—and know exactly what you’re missing.
The Graylog Input Wizard helps you quickly set up new data sources, but it also goes a step further: as you select use cases to support (e.g., lateral movement, privilege abuse), it flags any missing log types required for full coverage. This ensures your detection goals are aligned with your available data—before an alert even fires.
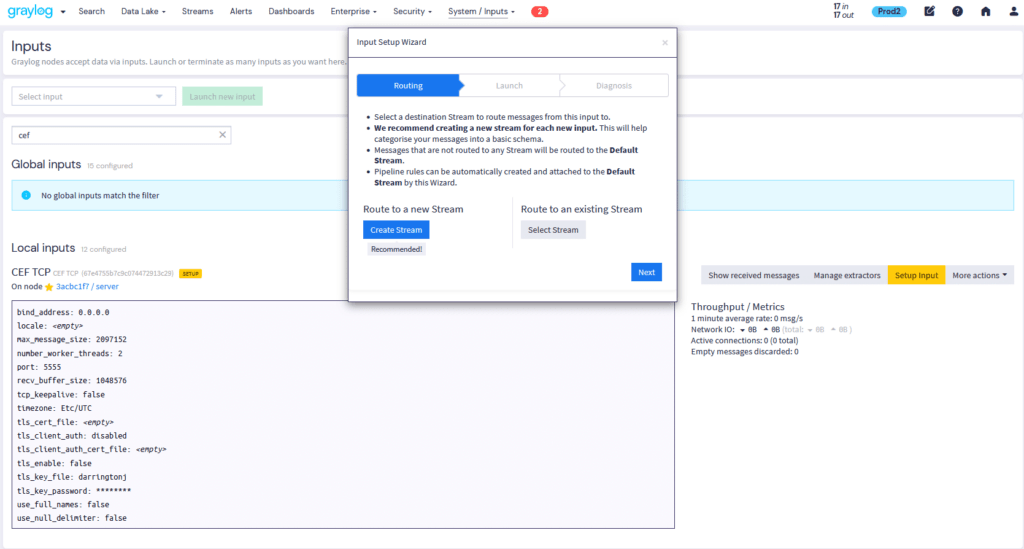
Input Wizard and Diagnostics Available in: Graylog Security | Graylog Enterprise | Graylog Open — Compare Plans
Easily discover, install, and manage prebuilt content.
See everything available in one place—what’s installed, what’s new, and what fits your environment. No guesswork, just fast enablement of useful content based on the data sources you have flowing into Graylog. With a clear, organized interface, you can quickly enable new sources, parsers, dashboards, and alerts.
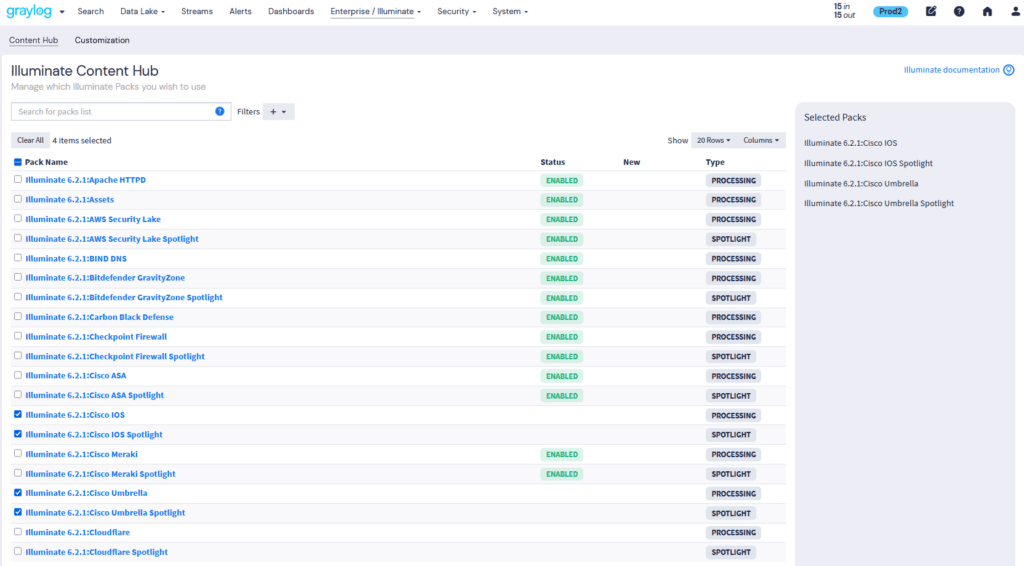
Illuminate Content Hub Available in: Graylog Security | Graylog Enterprise — Compare Plans
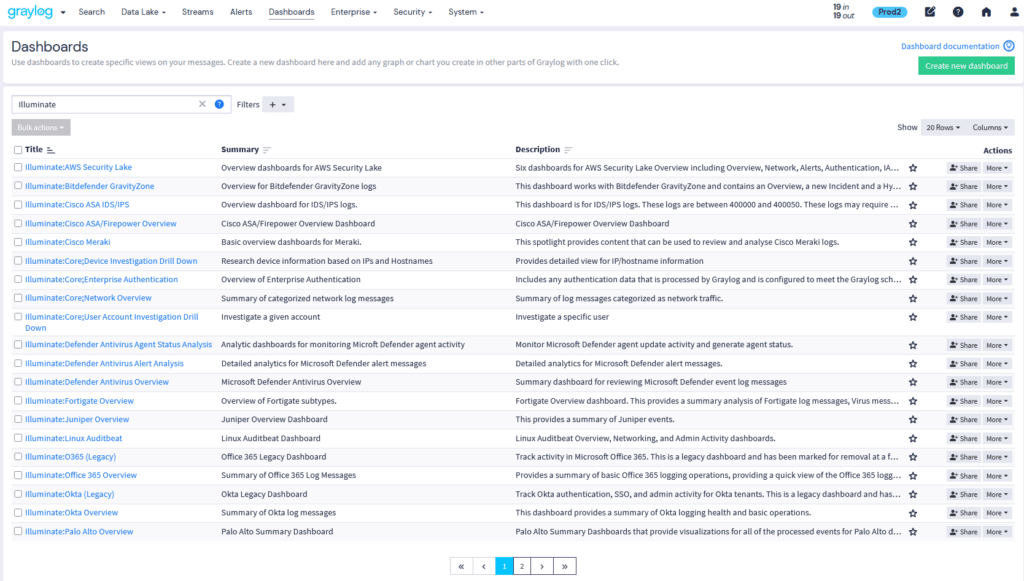
Illuminate Content Available in: Graylog Security | Graylog Enterprise — Compare Plans
Eliminate blind spots with out-of-the-box content for services like CloudTrail, Security Lake, and Azure AD. Improve visibility and simplify compliance from a single platform.
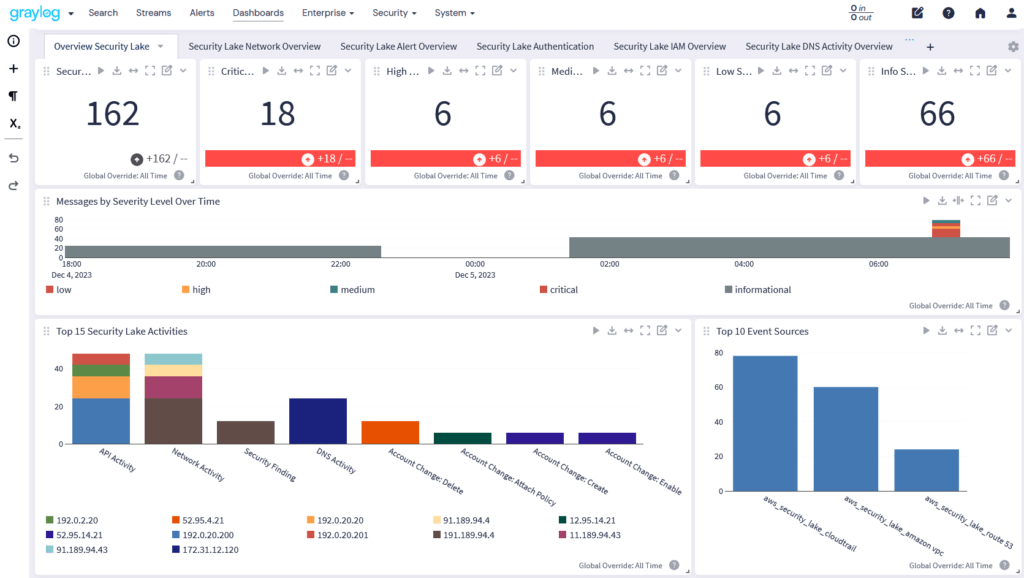
Illuminate Cloud Platforms for AWS Services, Graylog Cloud Platform and Microsoft O365 & Azure Available in: Graylog Security | Graylog Enterprise — Compare Plans
Graylog integrates with leading endpoint security solutions, enhancing threat detection and system monitoring:
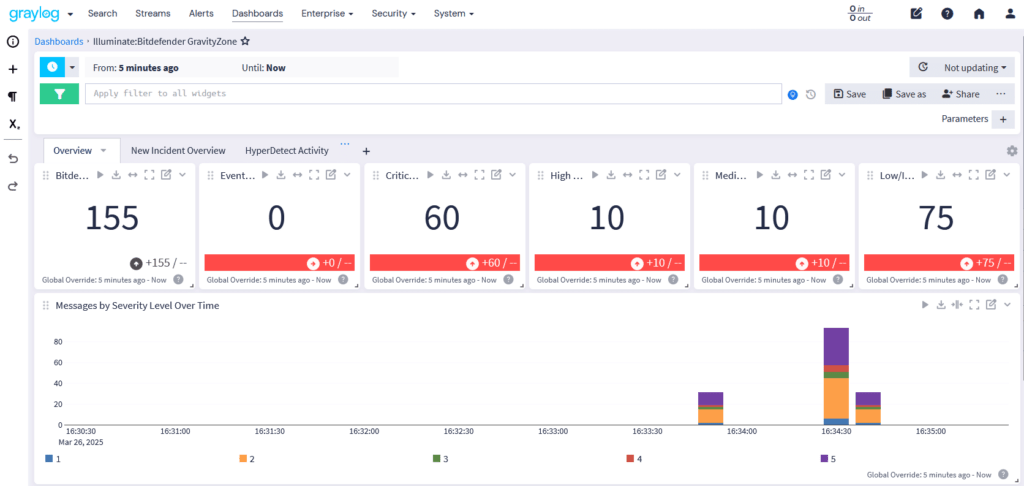
Illuminate Security & Endpoint Protection Available in: Graylog Security | Graylog Enterprise — Compare Plans
Centralized log management for firewalls, VPNs, and network security devices:
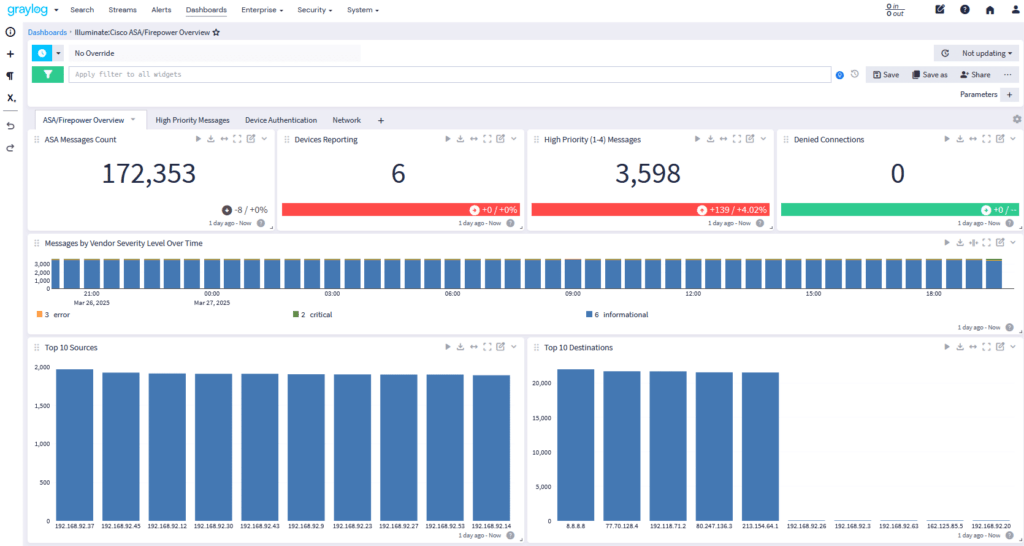
Illuminate Network Security & Firewalls Available in: Graylog Security | Graylog Enterprise — Compare Plans
Deeper visibility into system activities, security events, and operational performance:
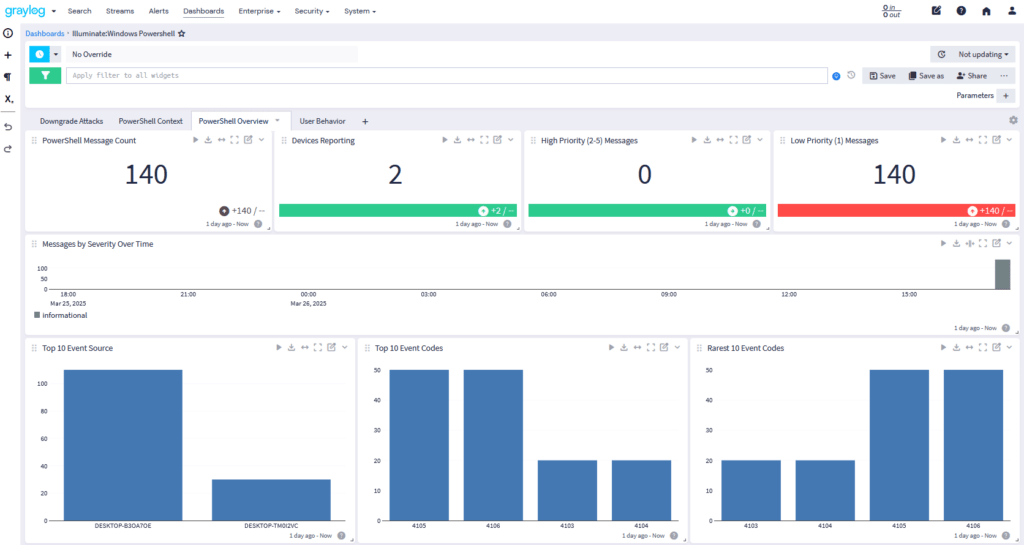
Illuminate Enterprise Applications & System Logs Available in: Graylog Security | Graylog Enterprise — Compare Plans
Make your unique sources searchable, structured, and scalable. Graylog’s Information Model (GIM) standardizes data across your environment. For unique sources, our Professional Services team can build custom content that aligns with GIM—ensuring consistency and searchability.
Custom Content & The Graylog Information Model Available in: Graylog Security | Graylog Enterprise — Compare Plans
Graylog integrates with cloud platforms, endpoint security tools, network firewalls, and enterprise applications to provide centralized log management, real-time threat detection, and compliance-ready security insights. These integrations enhance security by:
Graylog Illuminate is a framework that enhances log analysis by providing:
Illuminate helps security and IT teams better understand log data across cloud, hybrid, and on-prem environments, accelerating detection, improving reporting, and supporting more efficient incident investigations.
Graylog offers seamless security integrations with:
Graylog integrates with leading endpoint security solutions to improve malware detection, forensic investigation, and behavioral analytics. Supported tools include:
These integrations help security teams respond to threats faster by aggregating logs from multiple security solutions into one centralized SIEM platform.
Yes! Graylog provides centralized log management for network security tools, including:
By aggregating and analyzing firewall & VPN logs, Graylog detects suspicious activity, policy violations, and unauthorized access attempts in real-time.
Graylog enhances enterprise security by integrating with system logs from critical applications such as:
This integration helps IT teams quickly identify anomalies and proactively address security threats.
Graylog supports regulatory compliance and audit readiness by:
With Illuminate and built-in reporting features, Graylog helps security teams stay compliant and audit-ready with less manual effort.
Graylog improves threat detection through a combination of features designed to surface unusual or suspicious behavior across systems:
Together, these features empower security teams to detect and respond to threats faster, with clearer context and streamlined workflows.
Yes. Graylog is built to support modern security operations by integrating with XDR, MDR, and SOAR platforms in the following ways:
By acting as the central investigation and analytics layer, Graylog enhances the value of your XDR, MDR, and SOAR solutions while providing a unified view across all log sources.
To integrate Graylog with security tools, follow these steps:
With Graylog’s pre-configured security dashboards, teams gain immediate visibility into their security posture.