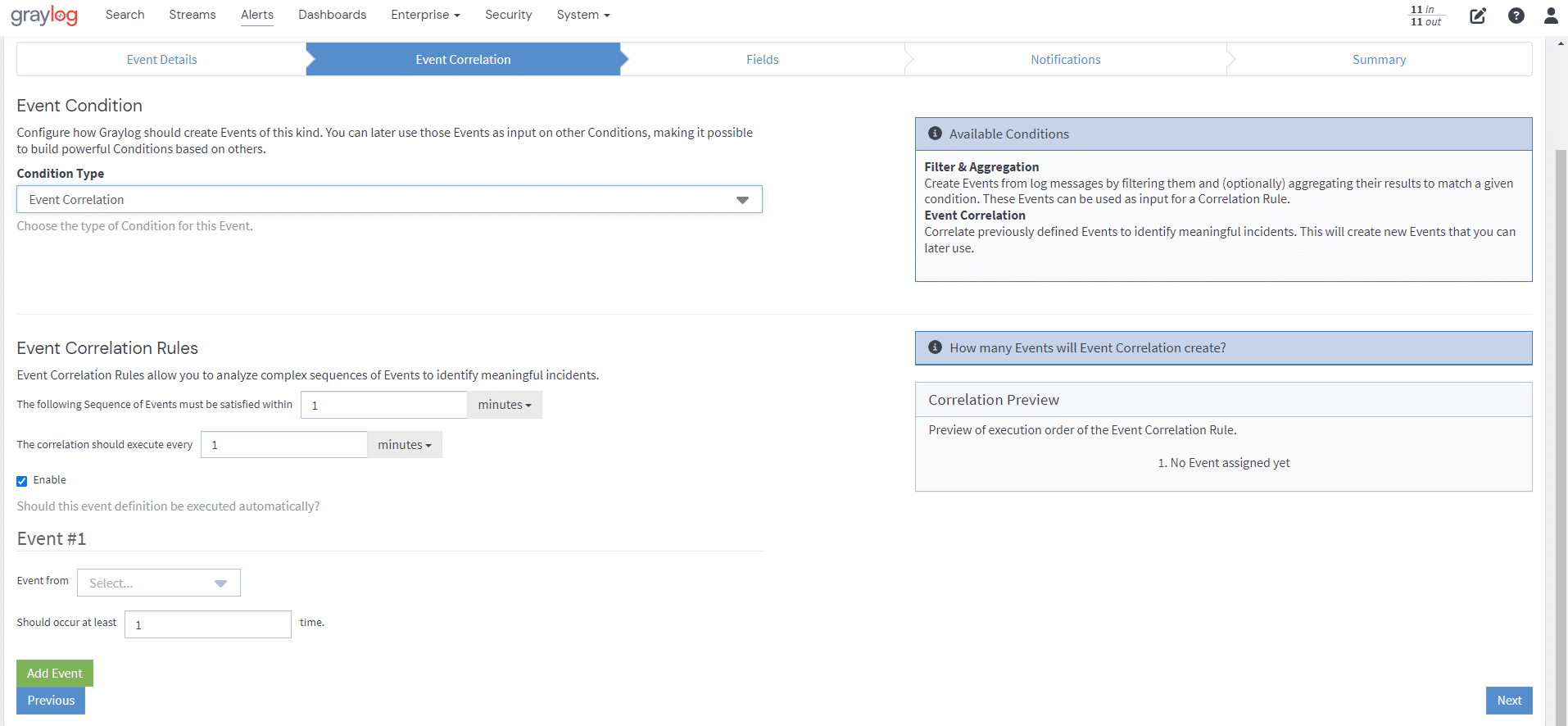
Graylog is monitoring all the logs as they enter the system, and based on defined event and alert rules, will take the logs of interest and move them from the noise into their own Elasticsearch index. With the high value logs in their own index, you can run queries on those events to see if there is a pattern of activity, or lack of activity.
Events and correlation events are stored in Elasticsearch, allowing for further filtering, aggregation or compound correlation rules, allowing you to build a very powerful alert from your data.