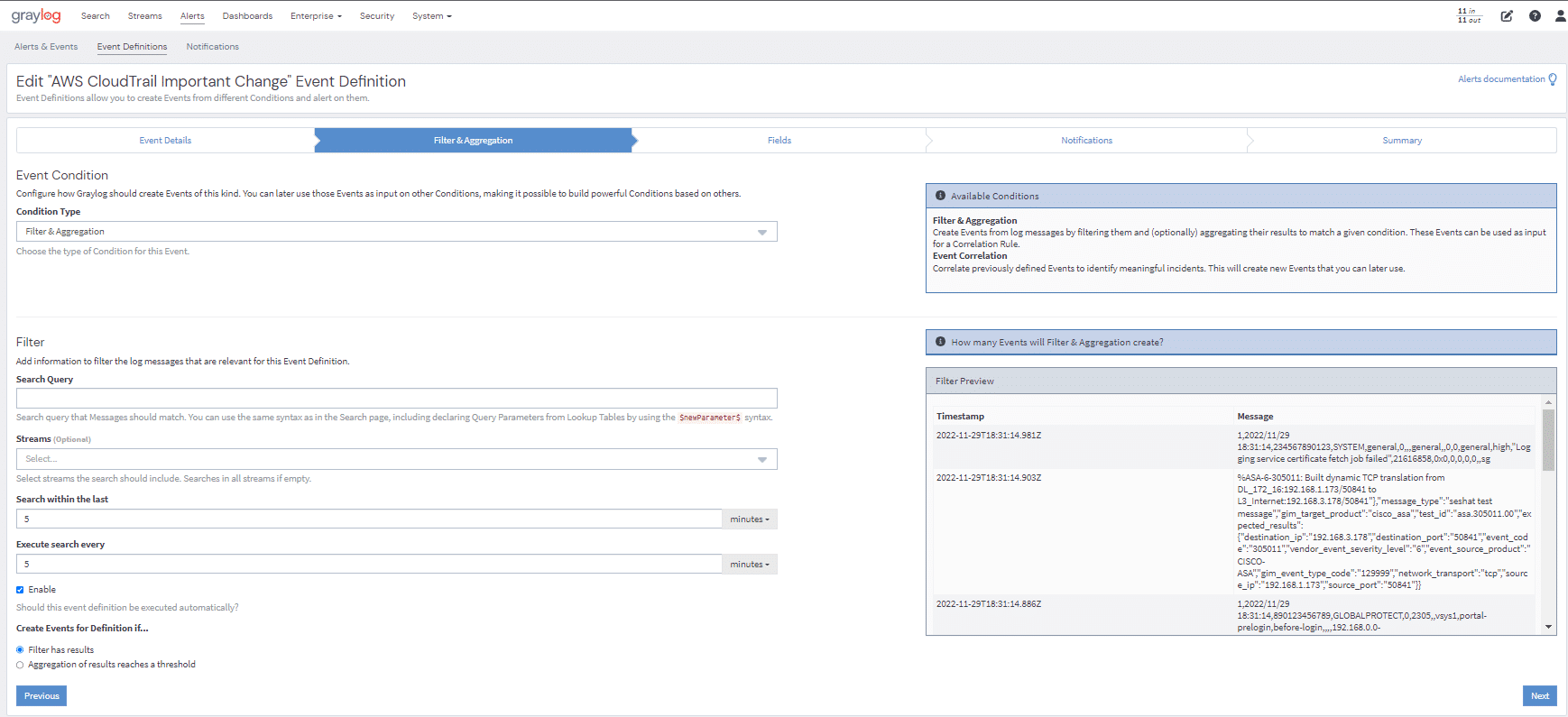
Graylog alerts are periodical searches that can trigger notifications when a defined condition is satisfied. You specify the alert conditions in which Graylog considers those search results as exceptional, triggering an alert in that case. Alert time frame can be set to only search a specific time in the past, as well as how often to perform the searches.
Graylog allows you to create any alert condition based on the data you are collecting. You can also extend alert conditions with plug-ins from the Graylog Marketplace. The default alert conditions are:
Aggregation Condition
Triggers when the result of a aggregation has been met through a statistical computation. Aggregation has been improved to have group by fields, allowing for individualized alerts per grouped field. Multiple groupings can be done per alert as well.
Filter Condition
Triggers when the stream receives at least one message since the last alert run that has a field set to a given value.
Alerts can be sent via email, text, or Slack.
Sigma Rules (Graylog Security)
Sigma rules are YAML text signatures that enable you to identify suspicious events in your environment by matching log events that might indicate adversarial behavior or cyber threats. These rules are essentially a collection of “search scripts” used to identify specific threats within your IT environment.
With Graylog Security, security analysts can add or bulk import multiple Sigma Rules at once directly from the SigmaHQ repository and use them for alert definitions.
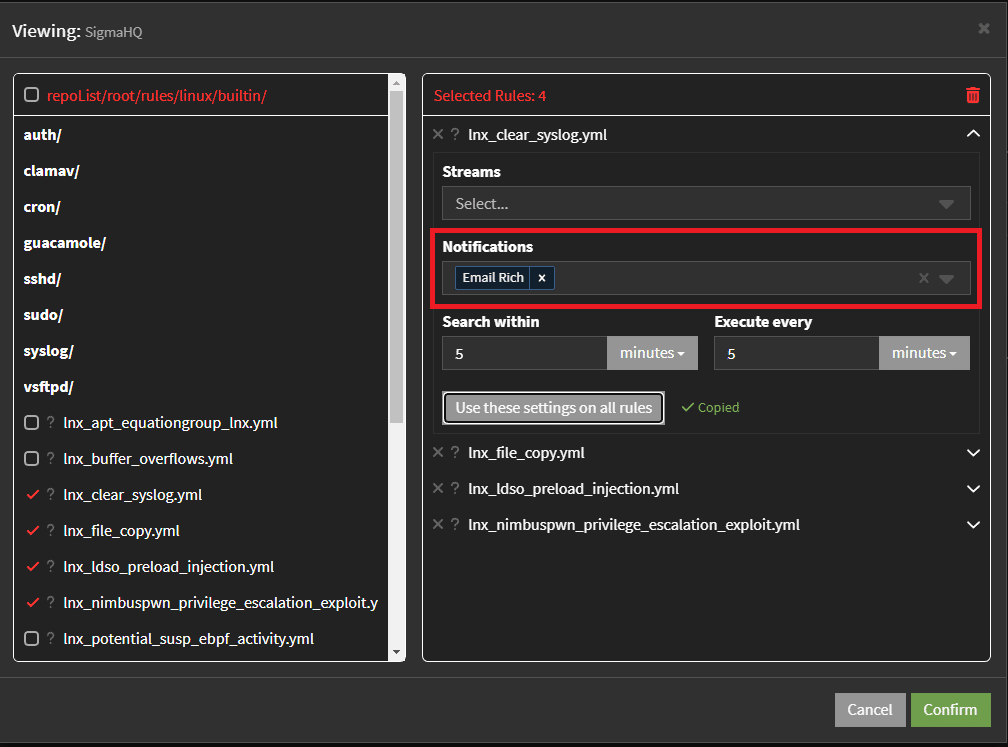
The bulk import of Sigma Rules into Graylog Security provides the following benefits:
- Analysts can configure multiple Sigma Rules to send an e-mail notification when an event fires directly from the import screen as opposed to manually editing all the notification definitions.
- A “Bulk Action” capability is available when selecting multiple Sigma rules that will allow analysts to assign a notification to one or more existing Sigma rules.

