Graylog Security
Empowering Your Cybersecurity with Advanced SIEM Technology
In the face of rising cyber threats, organizations urgently need efficient threat detection and incident response (TDIR). A robust SIEM solution is essential, not optional, for CISOs tackling the dual challenges of sophisticated cyber-attacks and cost management. Without it, companies risk data breaches, financial loss, and reputational damage. Effective SIEM systems provide comprehensive visibility and advanced analytics, which are crucial for defending against cybercriminals and ensuring business continuity.
A Robust TDIR Strategy Starts with SIEM
SIEM is the heartbeat of the SOC. It’s where everything comes together for a holistic security view of your organization’s entire infrastructure. Unfortunately, the market is saturated with traditional SIEM solutions that no longer meet the needs of modern organizations.
These outdated monoliths fall woefully short in the areas of:
- Cost Effectiveness: Traditional SIEMS can be expensive to operate due to compound costs associated with hardware, software licenses, maintenance, and convoluted communication of pricing strategies. This makes it difficult for CISOs to paint an accurate picture of annual cost.
- Analytics and Detection Capabilities: Traditional SIEMs often rely heavily on rule-based monitoring, which can be less effective against sophisticated, more modern threats. They also usually lack the advanced analytics and machine learning capabilities to detect and respond to complex, evolving cyber threats.
- Scalability: Traditional SIEMs often struggle with the vast amounts of data generated by modern and complex IT infrastructure environments, failing to scale efficiently to process and analyze data from a growing number of sources, leading to performance bottlenecks.
- Management and Maintenance: Traditional SIEMs can be challenging to manage and maintain with limited resources. They often require specialized knowledge and significant manual effort to update rules, parse new log formats, and maintain system health.
- Integration: Legacy SIEMs might have limited capabilities to integrate with newer security tools and technologies, creating silos of information and obscuring a unified view of security events across the organization.
SIEM Done Right with Graylog
Graylog Security is an advanced SIEM platform designed to optimize the Analyst Experience (AX) and help strengthen your organization’s security posture by:

USE CASE
Curated Threat Coverage
Decrease your risk with Graylog Security by aligning threat detection coverage to meet your security objectives with the following features:
- Graylog Illuminate content packs provide a library of curated event definitions, alerts, and dashboards for targeted security and log management use cases.
- Alert and event management capabilities make assigning exceptions, status updates, and notes to individual alerts easy.
- Prioritize alert triage more efficiently with risk-based scoring capabilities that automatically assign risk scores to individual alerts so analysts know what to focus on.


Identify
Graylog Security simplifies incident investigations. Whether collaborating across teams throughout your organization to synergize investigation efforts, identifying trends using data saved from prior investigations, adding important artifacts to an investigation as you research the incident, or automatically providing remediation steps so analysts can execute a quick and informed response, regardless of their level of expertise. Graylog Security makes it all possible.
Prioritize
Graylog Security streamlines the incident investigation process, providing you with all the necessary information to promptly and efficiently respond. With Graylog Security, you can seamlessly collaborate across teams within your organization, identify trends using data collected from previous investigations, and promptly add critical artifacts to your investigation as you research the incident.


Respond
Graylog Security simplifies the incident investigation process from start to finish so you have all the actionable information you need at your fingertips to execute a quick and informed response. Whether collaborating across teams throughout your organization to synergize investigation efforts, quickly identifying trends using data saved from prior investigations, or quickly adding important artifacts to an investigation as you research the incident, Graylog Security makes it all possible.
Evaluate & Evolve
Graylog Security helps you understand your cyber resilience by measuring critical security operations KPIs that represent how effectively you mitigate risk so you know where to focus improvement initiatives.

USE CASE
Efficient Data Management
Reduce your TCO with Graylog Security by ensuring optimal storage opportunities:
- Data tiering provides a “warm” storage tier that enables less expensive remote or on-premise storage options while providing the same lightning-fast and robust search experience as if data were in “hot” storage.
- Index field type profiles help manually assign profile types to fields within indices without needing API calls to OpenSearch.
- Enhanced archival performance helps optimize archive speed and efficiency.
Graylog Security
Built on the Graylog Platform, Graylog Security is the industry’s best-of-breed TDIR solution. It simplifies analysts' day-to-day cybersecurity activities with an unmatched workflow and user experience while simultaneously providing short- and long-term budget flexibility in the form of low total cost of ownership (TCO) that CISOs covet.
Graylog Security is designed to be a robust, scalable solution capable of helping analysts detect and respond to the cybersecurity threats of today and tomorrow.
USE CASE
Guided Analyst Workflow
Reduce key metrics like mean time to respond (MTTR) with Graylog Security by quickly resolving the alerts that matter with the following features:
- A unique security-focused UI tailored for analysts to quickly access investigations, alerts, and reporting workflows.
- Gain insight across your environment with the ability to track different assets and enrich log messages with contextual information.
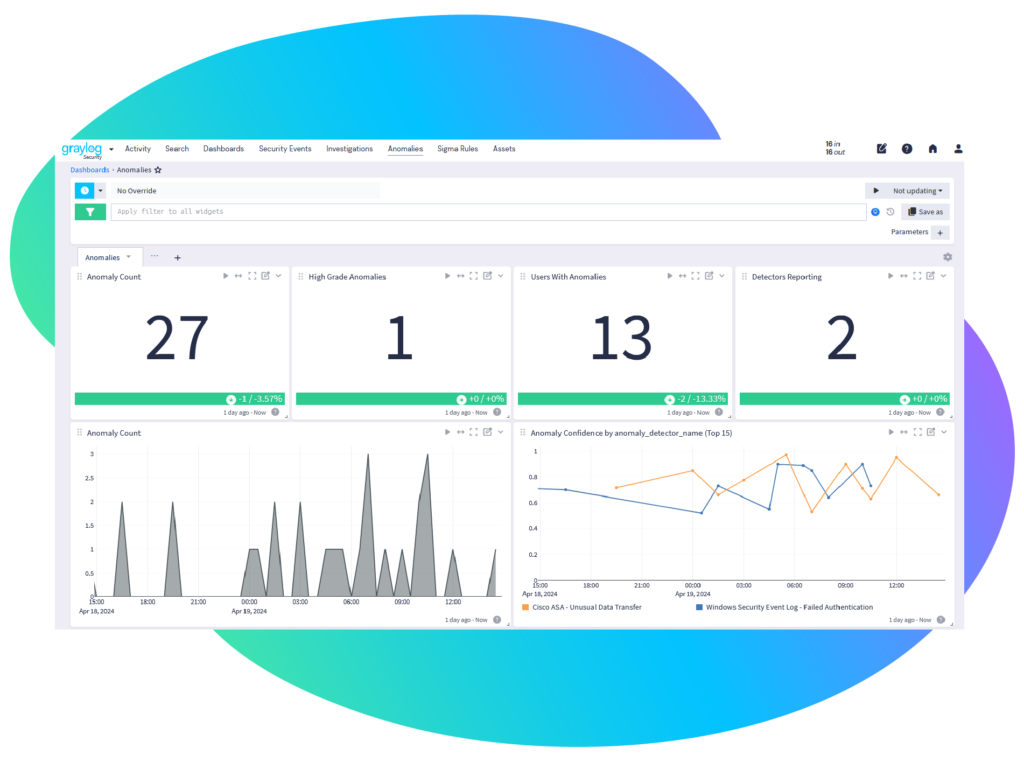
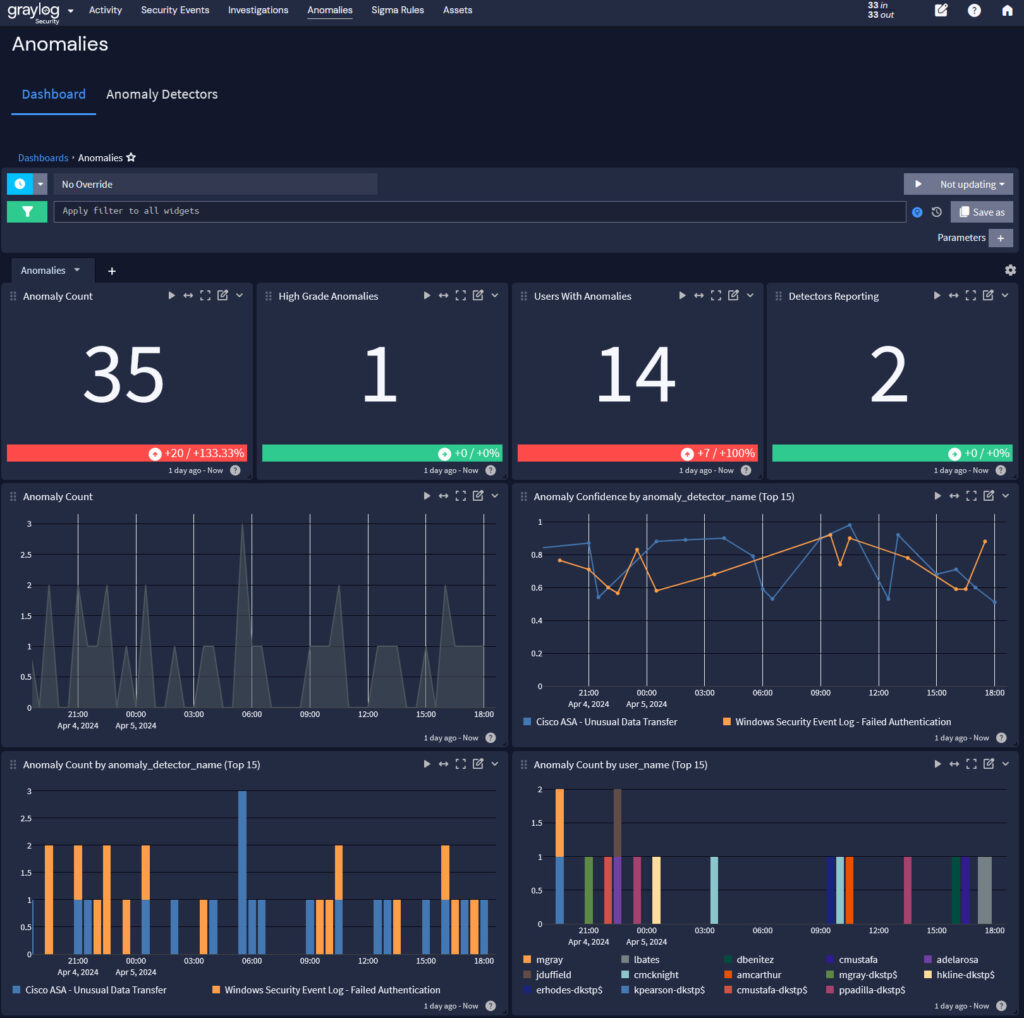
- Anomaly detection capabilities quickly learn “normal” behavior and automatically identify deviations for users and entities at scale, with continuous fine-tuning and improvement over time.
- Alert and investigation widgets allow a graceful way to filter and sort open investigations and raised alerts for streamlined triage.
- Enhanced investigation workflow and workspace provide more actionable information and context for expedited incident response.
- Search query string history reduces the effort in executing pivot searches or returning to previously unsaved queries.
- Leverage Graylog Security’s dashboard functionality to build and configure scheduled audit and regulatory compliance reports quickly.
- SOAR integration capabilities make sharing data with other business critical systems easy for full transparency and collaboration.