It’s that time of the year again. The annual and dreaded IT and security audit is ramping up. You just received the documentation list and need to pull everything together. You have too much real work to do, but you need to prove your compliance posture to this outsider. Using log management for compliance monitoring and documentation can make audits less stressful and time-consuming.
WHY DOES COMPLIANCE MATTER?
You’re on the front lines, working in the IT department. Left and right, help desk tickets are coming in, and alerts are firing. Compliance feels like one more burdensome task. On the other hand, senior leadership needs to prove that they’re complying with the regulations and standards governing your industry.
While compliance may feel like extra work, it offers several benefits for most organizations:
- Customer trust: Customers often require audit reports as part of their due diligence and third-party vendor risk management.
- Baseline best practices: Organizations can use compliance to double-check their cyber hygiene.
- Cost savings: Compliance violations lead to fines and penalties.
Since compliance has a business value, you need to find a way to fit monitoring and documentation into your daily activities.
WHY IS COMPLIANCE CHALLENGING?
Most likely, your company doesn’t just need to prove that it’s compliant with one regulation or standard. Most industries incorporate multiple requirements. While some have overlapping controls, others may be more prescriptive.
EXAMPLE
A healthcare provider who allows patients to pay their copay must comply with the Health Insurance Portability and Accountability Act (HIPAA) and the Payment Card Industry Data Security Standard (PCI DSS). While HIPAA focuses on protected health information (PHI), PCI DSS focuses on cardholder data. Although there may be overlaps between them, there are significant differences.
EXAMPLE
A government agency needs to meet compliance mandates like the Federal Information Security Modernization Act (FISMA) and the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 for securing controlled unclassified information (CUI). Although agencies need to use NIST 800-171 to comply with FISMA, FISMA also includes additional requirements beyond what NIST sets out.
WHAT IS SECURITY LOG MANAGEMENT?
For cybersecurity compliance, security log management means collecting event logs to monitor abnormal activity across networks and systems. Log files give you visibility into security events to help detect threats across on-premises, cloud, and hybrid environments.
Additionally, an organization can use tools like a centralized log management solution to collect the data needed in an audit.
FITTING LOG MANAGEMENT INTO THE COMPLIANCE PROGRAM
You use your logs every day and understand their value. Whether you’re on a small IT team that needs to manage security or a security team that needs visibility into risk, centralized log management gives you the data that helps you secure your environment.
WHAT YOU NEED TO GET COMPLIANT
Compliance mandates act as a set of baseline security controls. While the details around best practices may change from one mandate to another, the general categories of controls remain similar. For example, compliance requirements likely include:
- Access management
- Network security
- Endpoint security
- Patch management
- Encryption
- Continuous monitoring
The good news here is that you have all the data that helps you monitor and prove your compliance with many of these with log management. Since each requirement is based on a technology in your environment and each technology generates event logs, most of your compliance documentation lives directly in your centralized log management solution.
EXAMPLES OF EVENT LOGS THAT ENABLE COMPLIANCE
Let’s take a look at some of the ways you can uplevel your security and compliance programs with log management.
Event logs give you documentation around important security functions, including:
- User access to resources
- Virtual Private Networks (VPNs) and Firewalls
- Malware alerts
- Internet of Things devices
USING CENTRALIZED LOG MANAGEMENT TO REPORT COMPLIANCE
While compliance may start with the technical controls, that’s not where it ends. All compliance consists of the three letters GRC:
- Governance: Proving that leadership knows what’s going on and can make meaningful decisions
- Risk: Evaluating the likelihood of a data breach and the potential impact
- Compliance: Making sure that all controls meet the standards set out in the requirements
The risk and compliance parts are challenging on their own. However, governance is difficult when you’re a technical person trying to communicate with someone who doesn’t speak the same language as you.
Centralized log management solutions, like Graylog, give you a way to bridge that language gap. With dashboards, you can create visualizations – like pie charts or bar graphs – that make it easy to communicate the technical details in an easier-to-understand way.
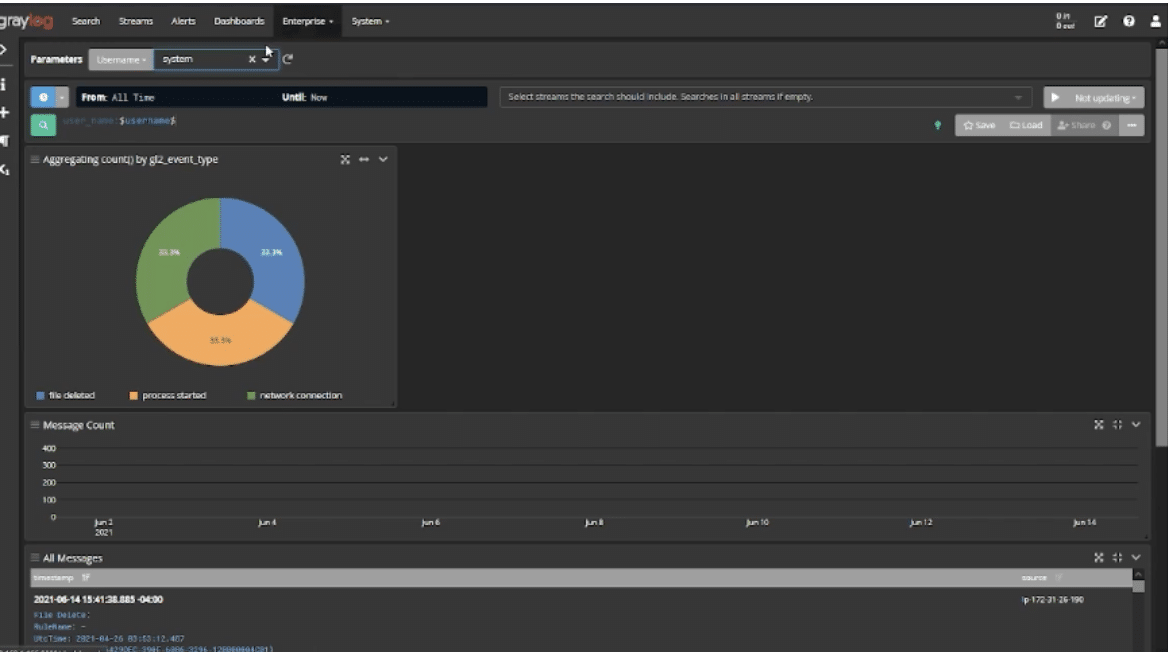
For example, Parameterized Dashboards can tell the story about how well you’re managing user access and data sharing:
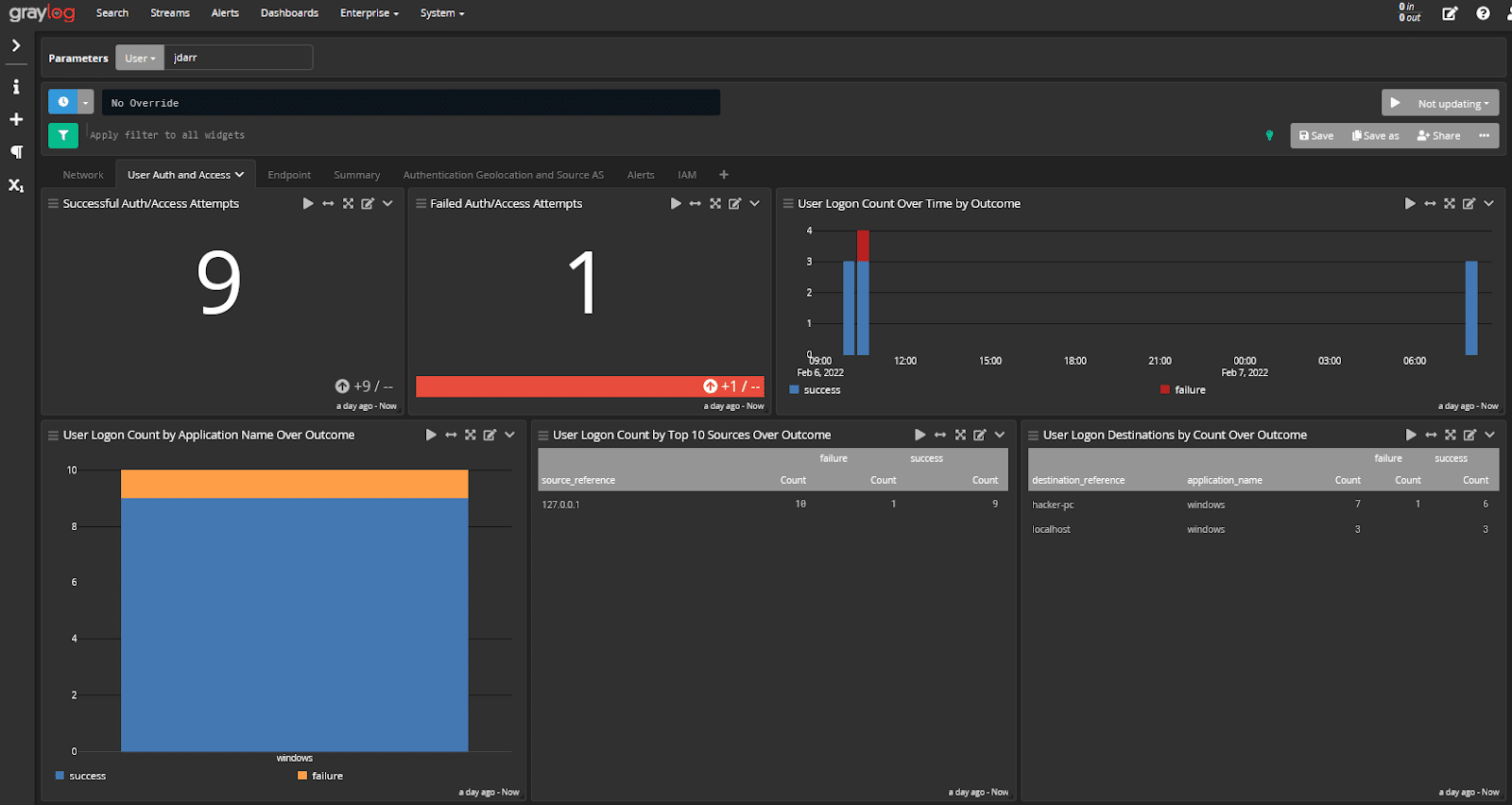
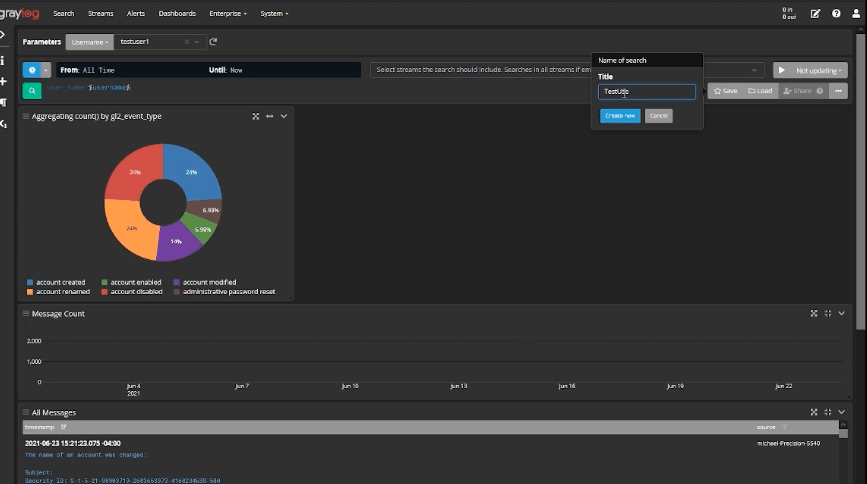
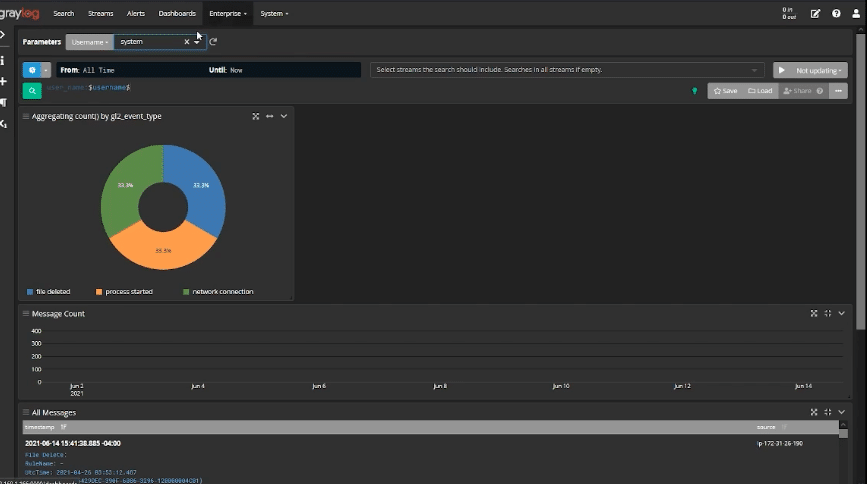
Senior leadership can see how many accounts were created, how many privileged accounts you have, or how many files were downloaded. Leadership gets the information they need without getting mired down in the technical details.
Dashboards can be set up as reports that answer critical security questions. You can forward them on a set schedule to meet compliance reporting requirements as part of your documentation.
By communicating effectively with leadership and the Board of Directors, you can get to the “G” of GRC more easily.
GRAYLOG FOR COMPLIANCE
You probably already know that log management helps you secure your environment. However, with the right centralized log management solution, you can also get rid of the drudgery – or at least some of it – that comes with compliance.
Unfortunately, compliance isn’t just “here to stay.” The increased number of data breaches means that legislatures are only going to add more laws, and those laws will be even more strict.
Graylog’s centralized log management solution gives you a way to easily translate the daily work of security into meaningful reports that help you prove compliance. Our solution makes creating dashboards easy and sharing them even easier. Our lightning-fast search capability helps you investigate incidents faster, while our dashboards create the proof that you contained a threat as quickly as you could.
Compliance doesn’t have to be a burden. Graylog’s capabilities can reduce the time and effort spent on compliance so that you can focus on your daily security tasks.