As an IT operations manager, you spend a lot of your time mitigating service outages and service level risks. You worked diligently to get the right people, products, processes, and partners in place to meet your goals. You managed to ensure continued uptime. You’ve reduced the number of tickets and the cost per ticket. And for your efforts, you’re rewarded with managing your company’s cybersecurity program. The problem? You’re not a security specialist.
With centralized log management, you can apply the principles of service design in operations management to enhance security without spending more or needing to learn new skills. In other words, your centralized log management solution gives you a “twofer,” acting as two tools in one.
Applying Service Design to Cybersecurity: You Know More Than You Think You Do
Managing operations and security is sometimes overwhelming for even the most experienced professional. But don’t panic. The details you need to identify security incidents are in the service tickets. For example, a password reset ticket might be an actual forgotten password, or it could be the first in a deluge of tickets signaling a brute force attack.
Consider the overlap between service and cybersecurity program design.

Not only do these look a lot alike, but they also work a lot alike. Even better, you can use your centralized management solution to help both processes.
Using Centralized Log Management for IT Operations Service and Cybersecurity
You already know the value that centralized log management brings to service quality and customer satisfaction. You can regularly monitor systems’ log files as part of your risk mitigation strategies.
You might have even incorporated log analysis into your daily tasks. For example, you probably already do things like:
- System monitoring: reviewing servers and hardware components for problems like server uptime and CPU performance
- Dependency monitoring: reviewing applications running across network nodes, components, and services by evaluating incoming traffic
- Application performance monitoring: reviewing resource consumption, error rates. App response times and request rates
- Integration and API monitoring: reviewing integrations for data processing, resource capacity to identify availability and uptime
The good news is that a lot of the monitoring to enhance customer experience can also help you with your cybersecurity. This means that if you’re incorporating these reviews into your daily tasks as part of IT operations risk mitigation, you can also start working towards up-leveling your cybersecurity program.
Using Your IT Teams Log Management Skills for Cybersecurity
In a lot of ways, cybersecurity monitoring and incident response start from the same place that service starts – analyzing event logs. Everything you need to know about security incidents can be found by aggregating, correlating, and analyzing logs. In fact, most Security Incident and Event Management Systems (SIEMs) actually use the logs generated by systems, networks, and applications.
Your IT team can take their log management skills to help mature your cybersecurity program and can help you build out a more robust cybersecurity program.
Continuous IT and Security Monitoring with Workflows and Parameters
Frankly, risk mitigation is risk mitigation. Whether it’s service or cybersecurity risk, you need to continuously monitor for potential problems. Suppose you’re using a centralized log management solution that parses event log data on the front end. In that case, you have a way to run continuous searches for better operational and security outcomes.

Everything you do to monitor your service and cybersecurity risks start with daily searches.
Whether you’re trying to proactively solve operations issues or enhance your security incident detection capabilities, you need to put practices in place that include daily reviews. Start looking for what you don’t know exists in your environment.

If you’re running manual queries against raw data, your searches will take a lot of time that you don’t have. Starting every day by spending an hour – or two or even three – running these searches isn’t an efficient way to spend your time.
With an intuitive centralized log management solution, you can view and find new research avenues at the click of a button to continually enhance operations and security.
Graylog Workflows and Parameters Support IT Operations and Cybersecurity
Graylog parses data on the front end, so you can build searches out in advance and schedule them to run regularly. By building the query in advance and scheduling it to run daily, you can get the services and cybersecurity insights you need without a lot of effort.
If you want to save a query as a dashboard to monitor the situation further, you can do that, too. For example, you might notice a network service issue and want to continue to monitor the situation without rebuilding the query. And the good news is, you can use this for operations and cybersecurity.
From the operations side, you might want to consider monitoring network statistics because they give you advance warning on poor performing network equipment or a possible redundancy failure that leads to a flood of help desk tickets. From a security perspective, you might want to monitor a network device that needs to have a security patch installed.
The more your teams can use event log data effectively and efficiently to detect system or cybersecurity issues, the better your operations and security programs are. By building and scheduling search queries in advance, you can automate daily service and security risk monitoring for a proactive approach to both.
Use Case: Monitoring an IP Address
Monitoring IP addresses is fundamental to network performance and network security.
From a network performance perspective, it can show important data about a destination IP like:
- Latency
- Jitter
- Packet loss
- Throughput
- Packet duplication
- Packet reordering
From a security perspective, it can show important metadata about a destination IP like:
- Active inbound and outbound connections
- Associated events
- DNS queries
- Unusual activity

Applying Known IT Ops Skills to Cybersecurity
If you start from the idea that you can pivot some of your service design and risk management activities to help address cybersecurity concerns, then you might not feel quite as overwhelmed.
These tools are often rigid and inflexible, which creates a barrier to entry for a lot of organizations. Whether arising from complexity of integration or a proprietary query language, it’s no surprise that this can feel overwhelming when you start your security journey.
Even more daunting is the feeling that you need to hire security-focused professionals who can manage these tools, increasing staffing costs. Whether you need to find someone with the right skills or invest in an employee’s training, experience with a tool is a hidden cost that increases the total cost of ownership.
Graylog Empowers IT Teams to Support Cybersecurity
Built with the practitioner in mind, Graylog doesn’t require specialized language or coding skills. This means that your IT team can take the log review skills they already have and apply them to cybersecurity.
With Graylog, you can handle many of your security needs without having to go looking for additional staff. For example, network monitoring can be either a performance or security activity. This is why, with the right parameters and search, you can use your centralized log management solution for both.
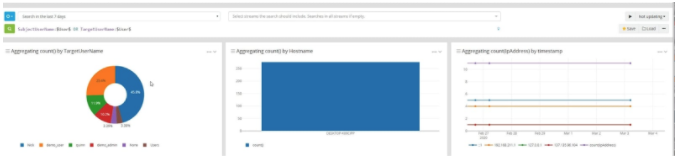
In the above picture, you can see what source and destination IP addresses are being monitored as well as what types of traffic flow are being logged. You can also see the amount of traffic by size in bytes over time. These two items give you insight into abnormal or excessive traffic being generated in the network. By seeing the IP sources, you can easily see who is generating the traffic and where the traffic is being generated.
With the power of Graylog Search, you can click on a source and very quickly drill into the logs generated by any one particular source in this dashboard.
Your team already knows how to use their log management tool, so take those skills and apply them to cybersecurity.
Graylog’s Centralized Log Management: Your Extra Set of Hands for Service Design and Cybersecurity
Graylog is the flashlight that exposes service and cybersecurity risks. With Graylog, it doesn’t matter if your IT team comes up empty. The real value here is that they took a proactive approach.
Graylog’s speed and easy user interface give users the flexibility and freedom to engage in these best practices without having to worry that they’re neglecting other duties. They have easy, fast access to all the data they need to explore efficiently.
With Graylog, you eliminate the specialized skills needed and time spent writing queries. Your IT team can apply their service risk mitigation skills to cybersecurity, creating a proactive approach to both.