Log messages – also known as event logs, audit records, and audit trails – document computing events occurring in IT environments. Generated or triggered by the software or the user, log messages provide visibility into and documentation of almost every action on a system. So, with all that in mind, let’s explore all the biggest log management challenges of modern IT and the solutions for these problems.
LOG MANAGEMENT ISSUES – LOG CORRELATION
Businesses – especially big ones – generate an astounding amount of data daily. So while most log management services can collect this data, the importance of log management lies in correlating data.
Log correlation is the process of making connections between events occurring in different systems or on different devices to help detect and investigate issues. With the right log analysis tool, you can bring together different log events that might otherwise seem unrelated.
Simply put, this is the difference between “good” and “bad” data activity. A false positive can seem like a big problem without appropriate protocols and advanced analytics in place. At the same time, a severe security breach can mask itself to appear as innocuous standard activity.
In this age of big data (that is becoming bigger and bigger with each passing second), log correlation is a vital part of log management – one that is used for everything from cybersecurity, system administration, and staying compliant with mandatory auditing procedures.
A solution with log correlation enables you to:
- Get high-fidelity alerts to weed out false positives
- Prioritize alerts based on risk level
- Use threat intelligence to help detect and investigate indicators of compromise
- Install content packs for sharing configurations with pre-built inputs, processing intelligence, display templates, alerts, and reports
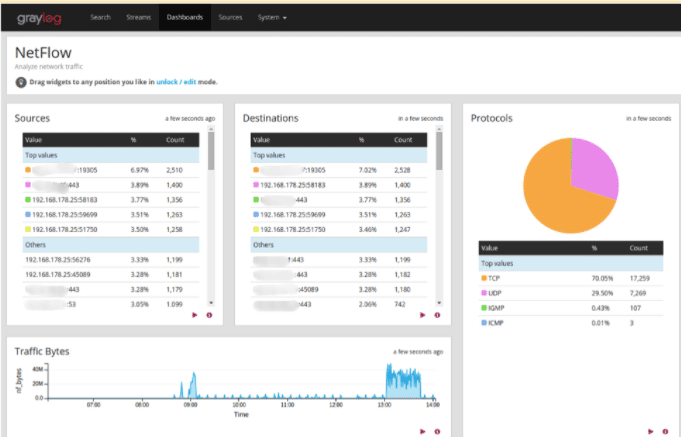
EXAMPLE
Netflow protocols show the throughput to destinations and devices, indicating percentages of packet types. Visibility into packetcount correlated with total throughput of an interface can give insights around application degradation.
LOG MANAGEMENT ISSUES – WHEN (AND WHAT) TO AUTOMATE
Like most types of software, Log management is heavily reliant on automatization. Data that is practically impossible to sort through by (human) hand is ordered, sorted, and analyzed by the program. Left to its own devices, your log management tool (LMT) will do its best to carry out the job according to its (pre)set parameters, but this is hardly an ideal solution.
New threats and problems are cropping up every day. While your LMT is designed to help you identify and deal with them, a dedicated human in charge of steering its functioning and setup is needed to bring out the real benefits of log management best practices.
Knowing what to automate and what to do by yourself is an acquired skill in itself. And, like any other skill, it requires practice, time, training, and human devotion to get the most of it.
EXAMPLE
Automating log management with a threat intelligence feed correlates threat indicators with real-time data coming from your log entries.
LOG MANAGEMENT ISSUES – STORAGE AND ARCHIVING
Archiving log files reduces the amount of data you have to keep on your local servers and hard drives. Depending on your needs and compliance requirements, log data is usually saved locally for up to 30 days. However, you may also want historical log data to identify the entry point of a problem or incursion that happened several months (or even years).
Although historical data is used for security and system problems, it’s primarily for auditing purposes. Some regulatory audits require you to keep your log data for three to five years, and others may even mandate it be saved, for all intents and purposes, forever.
These logs are compressed in a lossless format to reduce log size instead of being stored in their raw form. You can choose to import them into your program whenever you want to, or have to, make use of them. This makes auditing a much more painless and agile procedure.
One of the biggest problems here is scaling. Many log management solutions will charge you a flat rate which can vary wildly instead of charging based on how much data you process and store. The difference between ten and fifty users (or ten and fifty gigabytes) is staggering.
It is easy to go over the limit, and then you will have to pay for the more expensive package. A good log management tool will keep this in mind – with scalability being one of its core features and pillars of design architecture.
LOG MANAGEMENT ISSUES – LACK OF A USER-FRIENDLY INTERFACE
Few things can frustrate the user as much as an unintuitive, poorly made interface.
User experience is the foundation for how the user interacts with the application. A user interface (UI) that isn’t immediately clear and precise in its visual language can – and will – lead to mistakes, human error, and oversights.
A good user experience is built by thinking like the end-user and understanding:
- What data the end-user needs
- How the person uses the tool
- What workflow the end-user follows
- Different types of viewing options are needed, like graphs and pie charts
LOG MANAGEMENT ISSUES – REPORTING AND SEARCH FEATURES
Underdeveloped searching and reporting features are common problems plaguing many log management tools. With log file data that can easily measure in terabytes, having the option to perform an in-depth and fast search is of paramount importance.
Likewise, setting up reports has to be both intuitive and functional. Regardless of the time of day (or night), things can always go wrong. It is imperative that reports are sent out as soon as there is a problem and reach the right people in charge. Reporting also has to be customizable, with the option to send out daily/weekly/monthly reports by email as needed.
EXAMPLE
Multi-threaded search helps you quickly and efficiently find pertinent data. Search queries should be easy to perform and provide all-encompassing information in their results.
CONCLUSION
There are many issues and challenges when it comes to log management. While it is an indispensable part of modern IT, not every log management tool is created equal. Many lack the necessary, sometimes even basic, features required to provide a complete log management solution.
Graylog comes in both open source and commercial versions. It includes all of the above-discussed crucial features plus more. In sum, a full-scale flexible and extensible log management solution that adapts to your changing needs.