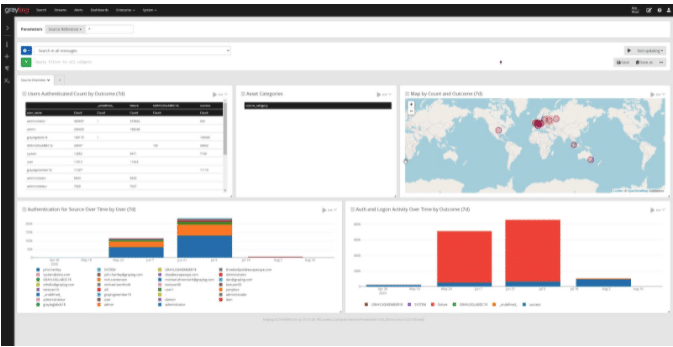
Struggling with the evolving cybersecurity threat landscape often means feeling one step behind cybercriminals. Interconnected cloud ecosystems expand your digital footprint, increasing the attack surface. More users, data, and devices connected to your networks mean more monitoring for cyber attacks. Detecting suspicious activity before or during the forensic investigation is how centralized log management supports cybersecurity.
WHAT IS LOG MANAGEMENT?
Logs are the files that detail all the events that occur within your company’s systems and networks, including servers, firewalls, and other IT equipment. Each device, system, network, and application is called a log source. The event logs can show deviations from expected activity, giving visibility into potential configuration, hardware, or security issues.
Logs provide data about a wide array of activities across the ecosystem, including application, system, audit, authentication, intrusion detection system (IDS), and intrusion prevention system (IPS) logs.
Example
You can monitor DNS server logs to see whether infected hosts are attempting to get an external malicious site’s IP address to communicate with it. A DNS server log identifying this type of malicious activity may indicate a malware infection.



Log management is the security control that centralizes all the generated log data into a single location. This creates more effective security monitoring and enables comprehensive auditing. Organizations can establish more robust cybersecurity programs with all log data optimized for visibility and stored in a central location.
WHAT ARE SOME FUNDAMENTAL LOG MANAGEMENT CHALLENGES ORGANIZATIONS FACE?
While log management is a fundamental security control, many organizations struggle for useful log event collection, review, and management. Digital transformation strategies only add to administrators’ burdens by regularly increasing the volumes of log data they need to review.
TOO MANY SOURCES
Many organizations struggle with log analysis because as they add more services to their IT stack, the volume of logs that administrators need to review also increases. Even more overwhelming, a single log source might generate multiple logs.
Example
Applications can create log events for both authentication attempts and network activity. As your organization adds to its digital footprint, it increases the number of log sources, leading to an explosion of log data that becomes difficult to manage.
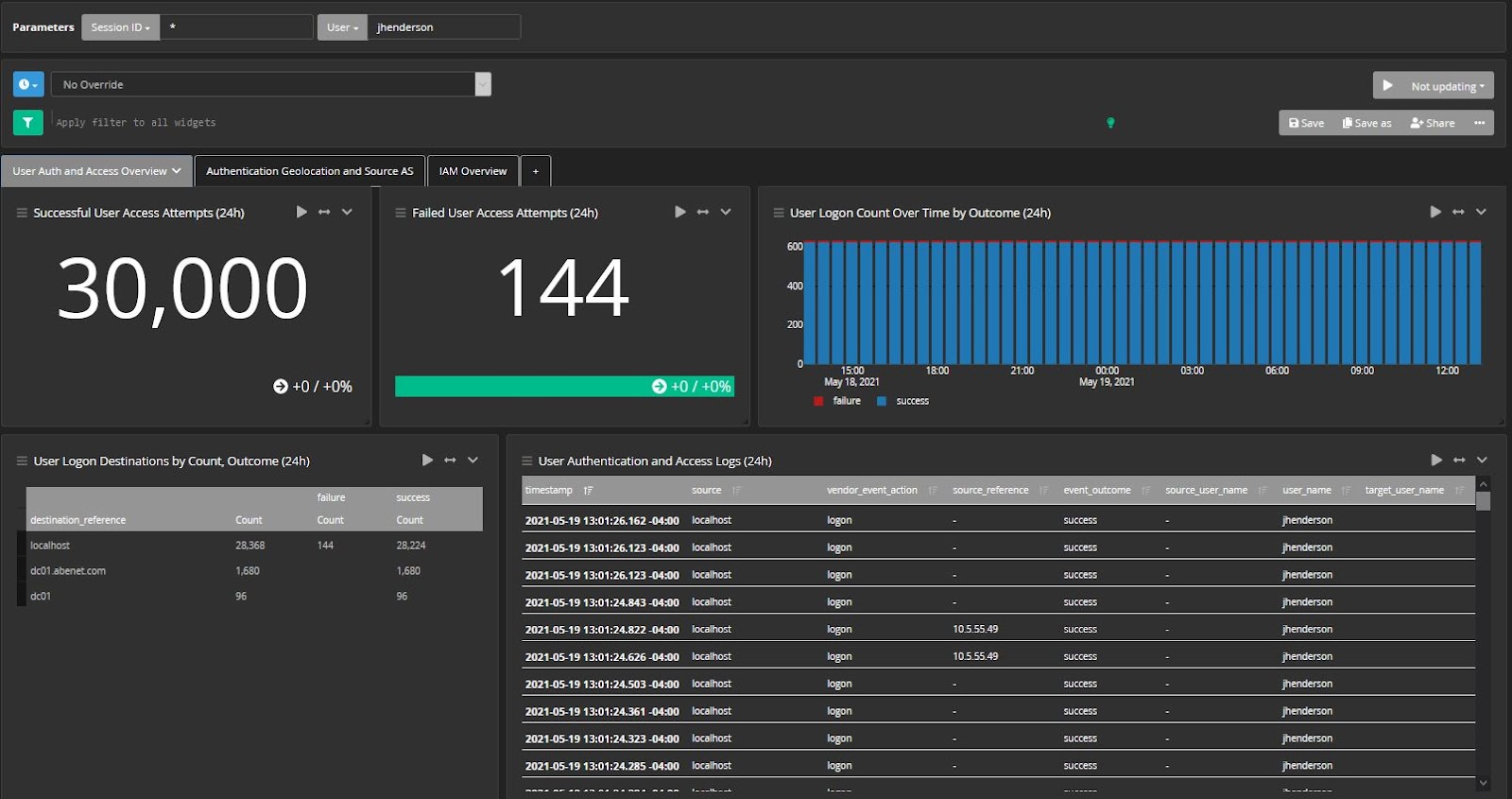
LOG DATA INCONSISTENCY
Log sources record only the data that they consider essential. This means that your DNS log may report different information than your operating system log. The various data collected and reported by logs makes it difficult to bring together all events in a meaningful way.
Example
If one source reports the source IP address while the other reports username only, bringing the two logs together to create a complete story of events becomes difficult.
TIMESTAMP DISPARITY
Every log source reports events using its internal clock. You may not be able to create a single, standardized timestamp across all logs, which sometimes makes correlating events more difficult.
Example
Suppose your authentication log indicates anomalous access two minutes before your IDS reports the same event. In that case, you may not be able to tie the potential security incidents when searching for the malicious actor’s point of entry.
LOG FORMAT DIFFERENCES
Many organizations struggle with log management because source types often use different formats. These include comma-separated or tab-separated text files, databases, Syslog, Simple Network Management Protocol (SNMP), Extensible Markup Language (XML), and binary files. This can make downloading and correlating information difficult since some formats may not align with others.
WHAT IS LOG MANAGEMENT INFRASTRUCTURE?
A log management infrastructure is the collection of all hardware, software, networks, and media that you use to generate, transmit, store, analyze, and dispose of log data. Although a wide variety of log management software exists, organizations typically choose either a Syslog-based centralized logging software or security information and event management software (SIEM) when creating a log management infrastructure.
You can better manage and prioritize alerts with the right log management infrastructure to create a more focused cybersecurity monitoring and risk remediation program. Log management infrastructures establish a single source of data that enables you to more efficiently and effectively detect, mitigate, and report cybersecurity risks.
SYSLOG-BASED CENTRALIZED LOGGING SOFTWARE
Syslog is a logging format that includes a header, structured data, and a message that applies a severity rating to the reported issue. Many organizations utilize Syslog because it is cost-effective, often free, way of collecting data across multiple applications and systems. Syslog contains details of individual applications that make troubleshooting easier without impacting application performance.
While Syslog offers flexibility, it is not perfect. Some challenges that come with a Syslog-based approach include lacking a standardized format, clogging the network, leading to lost messages, and no authentication processes to detect a device whose credentials have been stolen.
SECURITY INFORMATION EVENT MANAGEMENT (SIEM)
More organizations have adopted either agentless or agent-based SIEM software in recent years. An agent-based approach requires you to install the software agent on each host that generates logs so that the agent can extract, process, and transmit data to the SIEM server. The log-generating host transmits the data directly to the SIEM or intermediate logging server in an agentless deployment.
SIEM software automates the correlation and analysis process to streamline log management. Since it reduces the data, content, and timestamp inconsistencies, it provides more precise insight into and prioritizes logged events.
USING GRAYLOG MANAGEMENT FOR ENHANCED CYBERSECURITY
Log management supports a robust cybersecurity program by creating a single source of data for event reporting. You need to do more than identify abnormal events, and you need to document them for forensic purposes.
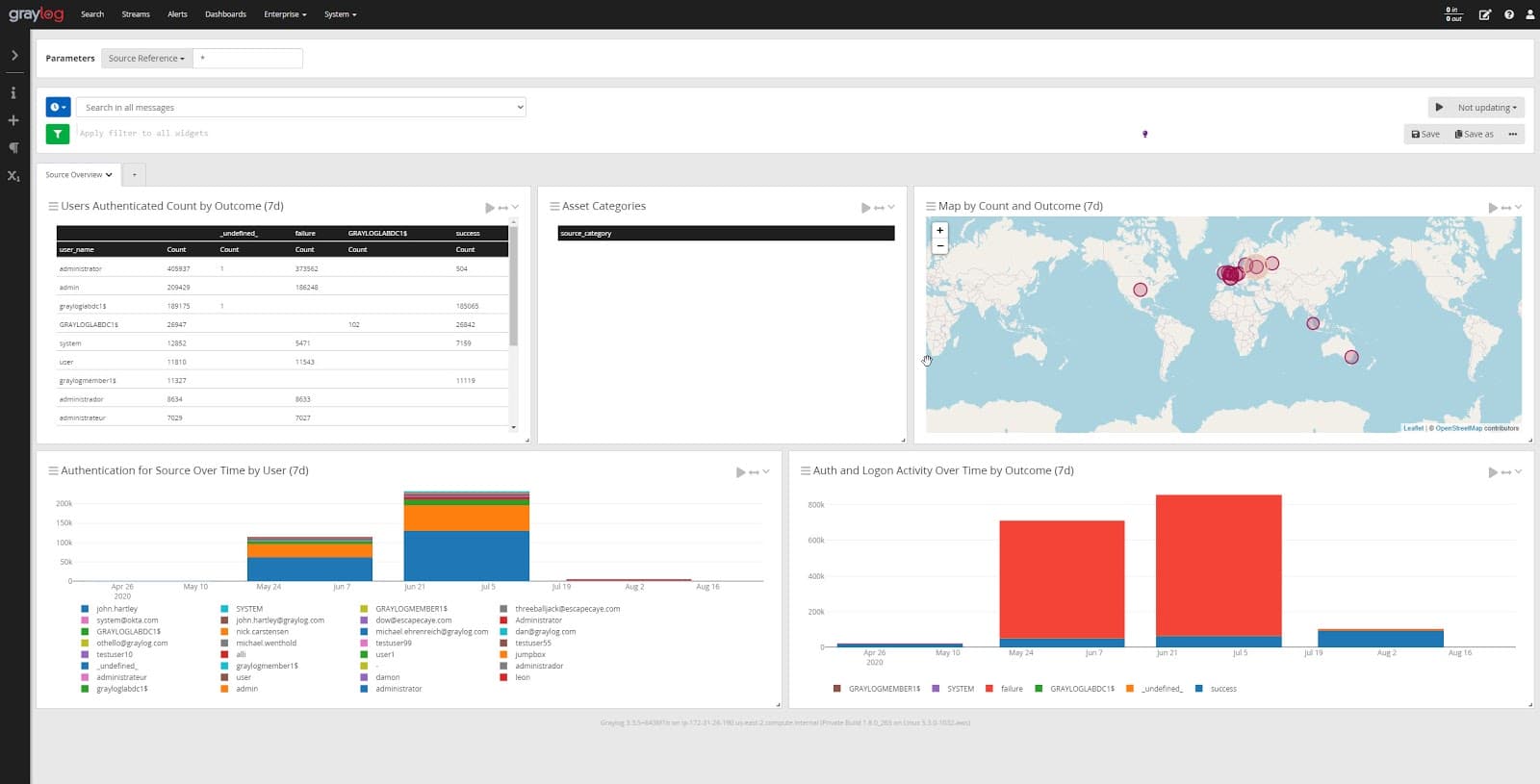
Graylog offers the most flexible and comprehensive approach to quickly detecting, responding, and hunting immediate security breaches. As cyberattacks will likely strike your enterprise at some point, drawing information from event logs will be instrumental in your cybersecurity strategy to mitigate them and reestablish your system to its normal operation.