So, you’ve done your homework. You’ve clearly defined business requirements, and you think you want to implement a Security Information and Event Management (SIEM) solution into your organization. Cloud migration and remote work have changed the way threat actors attack, and it feels like every day you read about a new methodology. While a lot of companies added a SIEM to their cybersecurity technology stack, you’re not sure whether you can afford one.
With 44% of organizations looking to replace or augment their current SIEM strategy, you should consider a few additional questions before making a final decision, like:
- Do you really need one?
- Are there other options?
Does my company really need a SIEM tool?
SIEMs are not plug-and-play solutions, and they are not cheap nor simple. Yet so many companies implement them.
Why? For a long time, SIEMs were the only way to get all the security information companies needed. In a world of constant security breaches and attempts at breaking into sealed networks, having a quality SIEM tool was viewed as the only way to get the visibility and analytics that could protect an organization.
Apart from that, companies also saw the other benefits the tools offered, including:
- Log management
- Monitoring and incident response
- Ticketing system integrations
- Policy violations and enforcement validation
- Compliance obligations (for example, HIPAA, PII, COBIT 5)
- Certifications (ISO standards)
While SIEMs used to be the only tools that provided all of these capabilities, data analytics and cloud technologies have evolved over the years to give companies more options. Today, you can find a lot of the features you need outside the SIEM market without getting all the add-ons that may go unused.
Will the SIEM tool implementation be tricky?
SIEM implementations can be complex. It’s easy to choose a SIEM because it has the data analytics you want and the alerting functionalities you need, but most SIEMs go far beyond those. In fact, it’s part of the reason why they’re hard to implement.
Having the right people
Although a SIEM will have built-in configurations, these may not work for your organization’s needs. You need to have the right people in place to configure and monitor your SIEM. Without fine-tuning, you can find that you get too many false positive alerts which leaves your security team struggling to get efficient detections that allow them to investigate and remediate risks.
This is why a lot of companies opt for bringing in either a vendor-supplied professional or an outside consultant to help them with their setup. Often, a company won’t have the cybersecurity talent needed to set up dashboards, configure correlation rules, schedule reports, and enable alerts.
Getting the right plan in place
A SIEM deployment is a long-term project. Before you start, you need to make sure that you plan your implementation, taking into consideration:
- System architecture. Note dashboard and reporting systems, storage and indexing systems, and finally, log collection systems.
- Hardware needed. Take into consideration the number of log sources and a projected volume (events per second).
- Storage requirements and pick a suitable storage network infrastructure.
With the plan in place, you can then proceed with a server, software, and appliance installation.
Managing the hardware and storage costs
This is often the biggest challenge that companies deploying a SIEM need to overcome. Part of planning your implementation is knowing what you need. The other part is knowing whether you’re going to be able to afford it.
Hardware costs
To get the performance you need, the standard hardware may not be enough. This means that you might see your initial estimated costs pre-planning stage increase after you determine the hardware and storage you need.
Storage costs
The cloud is noisy, generating terabytes of information every day. For example, just some of the cloud technologies generating logs are:
- Microservices
- Containers
- Layers of infrastructure
- Orchestration
- Applications
- APIs
- Instances
- Nodes
- Gateways
- Hosts
- Proxies
Accelerated cloud adoption over the last few years changes the amount of data you’re collecting and storing. Based on your needs, the storage costs may outweigh the SIEM’s benefits.
Will I need to hire more people?
It’s highly likely you’ll either have to bring someone in or reassign one of your existing employees to fill a SIEM-exclusive role in your organization. When you deploy a SIEM, you typically need someone who can:
- Administer the service environment
- Know how to deploy the application to multiple sites
- Monitor the central infrastructure
- Design and customize the search queries using a proprietary language
- Develop dashboards, data models, reports, and optimize their performance
Hiring an information Security Specialist who can manage these tasks becomes expensive, with research indicating an average base salary of $81,614 per year.
Centralized log management doesn’t require specialized skills
If you can’t afford to hire someone dedicated to your SIEM, then this might be a reason to seek an alternative solution.
For example, your IT and security teams probably already know how to work with a centralized log management solution. If your centralized log management solution incorporates security analytics, then you can use it as a SIEM to achieve your security goals. If your use case doesn’t require many of the complex features that a traditional SIEM offers, then you can solve a lot of the cost issues by using something your people already know how to use.
Is a SIEM tool enough on its own?
SIEMs focus on security information which in traditional on-premises deployments made sense. However, cloud migration changes things a lot. While a next-gen SIEM can respond to some of these issues, complex environments that include remote work require the ability to aggregate, normalize, correlate, and analyze data from:
- Devices, including Internet of Things (IoT) and mobile devices
- Networks
- Firewalls
- SaaS apps
- User identity and access management tools
Centralized log management is built for flexibility
This is another area where focusing on a centralized log management solution with security analytics can help you save money and meet your security objectives.
Centralized log management solutions were purpose-built to collect, aggregate, parse, normalize, correlate, and analyze all event log data. Security logs are the foundation of a SIEM, but centralized log management was built to handle all your security and event log information. They ingest the same information, so using a separate tool for only your security use-case is often redundant.
What does a SIEM solution cost?
Great question! There are quite a few alternatives out there, some of them costing an arm and a leg, while others are not as expensive–some of these come as open source alternatives as well. And while the cost of a tool itself is not as scary as one might think, there are several additional costs you should be aware of:
- Implementation cost – We already mentioned that a vast majority of companies opt for bringing in an external advisor to set up the system. Even if you opt to deploy it internally, there will be expenses concerning time, manpower and additional training may it be required.
- Training cost – Keep in mind that after implementation your staff will need training, and then retraining if there is ever a change to the workforce.
- Additional staffing cost – Managing and monitoring a SIEM tool is often a full-time job, and whether done by an internal or external expert, both will cost.
- Recurring costs – These costs include ongoing tuning, licensing, upgrade, and bandwidth fees.
Centralized log management is more cost effective
With all of these extra costs, it’s a good idea to look at the tools you have now – or the ones that would provide a more cost effective solution to your problem. For example, if your current centralized log management solution isn’t working for your security needs, you can consider whether another one would.
If you’re considering replacing what you have with something that gives you a “two for one” technology solution, you should consider:
- Ease of implementation
- Ability to do search without learning a proprietary language
- Provider’s training opportunities
- Cloud deployment and storage capabilities
Will SIEM software work with my current system?
Usually, you’ll introduce a SIEM solution to an already set-up IT system, with devices and applications up and running. The problem is that your organization isn’t planning to stagnate. In legacy, on-premises environments, you purchased technologies with a long-term plan in mind. In cloud-based environments, you’re not going to have the same static technology deployments. As you adopt SaaS apps, you’re not using the same long-term software licenses. Today, you’re using dynamic virtual machines and containers.
A SIEM often takes standard log protocols like Syslog and PCAP, then uses its own information model, creating inconsistencies and preventing you from incorporating newer technologies.
Centralized log management is scalable
Meanwhile, your centralized log management solution was purpose built to aggregate and correlate the data across your environment. Where a SIEM may be rigid, your centralized log management solution is flexible. As your security needs shift and evolve, your centralized management solution meets you where you are today and where you need to be in the future.
Which features should I be looking for?
Apart from forensic capabilities, reporting, security events correlation, alarms, grouping, and storage, there are some other features that would be (very) nice for your SIEM solution to have:
- User and Entity Behavior Analytics (UEBA)
According to the 2022 Verizon Data Breach Investigations Report, 82% of data breaches involved the human element through stolen credential, phishing, misuse, or an error. UEBA helps combat this by giving you a baseline for how people usually use your resources so that you can identify abnormal activity.
For example, an individual who usually logs on to the system between 9am and 5pm during workdays trying to log in on Saturday at 2am is a giveaway that something is amiss. In this case, a user and entity behavior analytics would provide you with a warning that unusual or anomalous behavior is noted on your network.
- Threat Intelligence and Threat Hunting
Some SIEMs include threat intelligence feeds, but others may not. In some cases, you might want to incorporate threat intelligence feeds unique to your industry vertical. Threat intelligence and threat hunting capabilities give you a way to create a proactive security posture.
Threat actors work hard to evade traditional detections, so even with optimized configurations something might slip through. With threat hunting, you’re looking for potential abnormal activities aligned to known attack types.
- Machine Learning with Big Data Analytics
Data analytics capabilities have evolved significantly over the past few years. While SIEMs used to be the only tools to provide these capabilities, that’s no longer the case.
With the right machine learning engine, you can spend less time understanding your baseline and tuning the analytics. Since it keeps learning, your results get better over time, continually fine-tuning your alerts.
Data analytics with built-in use cases means that you don’t need to worry about hiring a data scientist or a specialized security analyst to deploy and monitor your models.
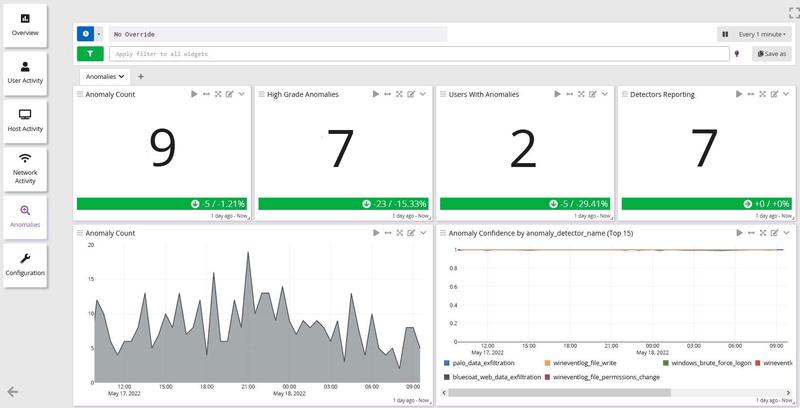
Graylog Security: The SIEM-plified Solution
With Graylog Security, you get the security analytics you need without the bells and whistles you might not use. You can get immediate value for your logs with cloud-native capabilities, intuitive UI, and out-of-the box content. As a centralized log management solution with security analytics, you don’t have to worry about hiring people with specialized skills or creating a silo between your security and IT operations teams.