Here at Graylog, we have recently had an increase in conversations with security teams from leading companies. We want to share our key findings with the Graylog community.
The good thing is that cybercriminals use a methodical approach when planning an attack. By understanding their process and knowing your network, you will be better prepared and able to stay one step ahead. In this blog post, we are going to review the 5 phases of intrusion and how to best combat attackers that are trying to infiltrate your networks and computer systems.
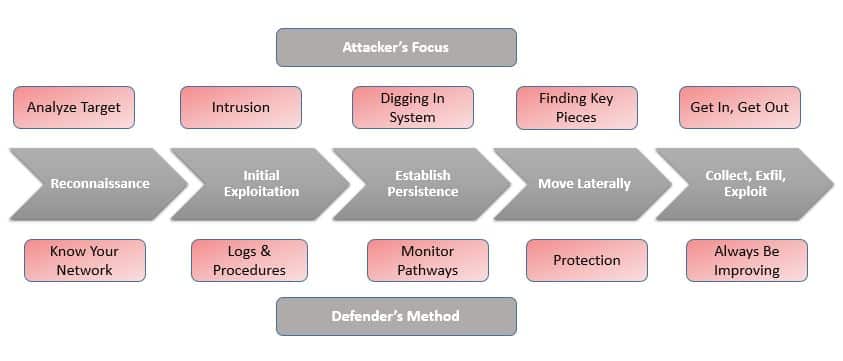
PHASE 1 OF INTRUSION: RECONNAISSANCE
ATTACKER’S FOCUS: ANALYZING THE TARGET
In this stage, attackers act like detectives, gathering information to truly understand their target. From examining email lists to open source information, their goal is to know the network better than the people who run and maintain it. They hone in on the security aspect of the technology, study the weaknesses, and use any vulnerability to their advantage.
The reconnaissance stage can be viewed as the most important because it takes patience and time, from weeks to several months. Any information the infiltrator can gather on the company, such as employee names, phone numbers, and email addresses, will be vital.
Attackers will also start to poke the network to analyze what systems and hosts are there. They will note any changes in the system that can be used as an entrance point. For example, leaving your network open for a vendor to fix an issue can also allow the cybercriminal to plant himself inside.
By the end of this pre-attack phase, attackers will have created a detailed map of the network, highlighted the system’s weaknesses, and then continue with their mission. Another point of focus during the reconnaissance stage is understanding the network’s trust boundaries. With an increase in employees working from home or using their personal devices for work, there is an increase in areas of data breaches.
HOW TO COMBAT: KNOW YOUR NETWORK
It is important to fully inspect your network, know the technologies inside, and any possible cracks in your system. The best way to fully understand the network and have information readily available for research is to centrally collect the log messages from your network hardware.
A tool like Graylog provides a visual of your network communications and path of connections using the one source of truth: log messages about established or rejected connections. Also, hiring a red team is a great way to put your security to the test. The red team will test your system to identify vulnerabilities in the infrastructure. If they successfully breach your network, they’ll show you which areas need more protection and how to correct the errors.
PHASE 2: INITIAL EXPLOITATION
ATTACKER’S FOCUS: INTRUSION
Persistence is key and infiltrators use numerous methods in exploitation. Water-holing is used by an attacker to compromise a popular website that is visited by company employees. Once the employee visits the infected site, the cybercriminal can attack their computer in hopes of gaining credentials and access to the company network. Other examples of vectors used by attackers is by spear phishing, SQL injection, infecting emails, and tainting removable media.
HOW TO COMBAT: LOGS AND PROCEDURES
To protect your system, you need to focus on the most detailed information about the network, the logs! Logs are the key to spotting any anomalies or breaches in your system. Having an enterprise-ready log management system, such as Graylog, will make it more difficult for cybercriminals.
You need to be constantly monitoring your network traffic and looking for anomalies and signs of attacks. Also, to make intrusion harder, among other measures, add two-factor authentication to the services your users use or implement the principle of least privilege as extra security methods.
PHASE 3: ESTABLISH PERSISTENCE
ATTACKER’S FOCUS: DIGGING INTO THE SYSTEM
At this point, cybercriminals are in your system and focused on gaining additional access to build up a presence. To take over the network, they will need to obtain more control and dive deeper into the system. One method is through privilege escalation. This is where the attacker uses any error or flaw in the system to either vertically or horizontally obtain extra privileges or ones that were not intended for the user. Other points of entry could be through open systems or finding SSH keys.
HOW TO COMBAT: MONITOR CONNECTION PATHWAYS
With the infiltrator in your network, most likely there will be a command and control channel from the outside into your infrastructure. Your task is to detect and disarm the control channel before the attacker can start to move laterally inside your network, causing more harm.
You can use network and operating system logs to find connections from the outside that should not be there. This should be a constant task that can be partly automated or managed with an easy to access dashboard.
PHASE 4: MOVE LATERALLY
ATTACKER’S FOCUS: FINDING KEY PIECES
Cybercriminals usually do not land in the exact spot of their target, thus, they need to move laterally to find their key pieces to complete their mission.
HOW TO COMBAT: PROTECTION THROUGHOUT NETWORK
If an attacker has made it inside your system, it is imperative to halt their movement. The amount of protection around your network needs to have the same strength as inside. You can strengthen your defense through network segmentation, monitoring your logs, and limiting administrator privilege.
PHASE 5: COLLECT, EXFIL, AND EXPLOIT
ATTACKER’S FOCUS: GET IN, GET OUT
The attackers have succeeded. They compromised your network and moved out your sensitive data. The attackers can now leak this information and the ultimate goal of their mission is complete.
HOW TO COMBAT: ALWAYS BE IMPROVING!
You need to be continually improving your defense systems, implementing policies and procedures, and always be analyzing your logs because it is the first place to detect malicious activity.
HOW TO MONITOR YOUR NETWORK LOGS WITH GRAYLOG
Our Graylog engineers are always helping the community by using log management to detect anomalies and hardening their infrastructure.



