When you engage in a security incident investigation, you need to quickly sift through vast quantities of data. In that moment, tracking your attacker, containing the attack, and identifying the root cause are the activities that matter most. However, in an attack’s aftermath, the digital recovery process and post-incident paperwork becomes your new nightmare. Between law enforcement and legal teams, you’re tasked with providing evidence about what happened, how it happened, and how you responded.
Digital forensics and incident response (DFIR) is the combined process of tracking down an incident’s root cause while preserving data so that it can be used as evidence.
What is Digital Forensics and Incident Response (DFIR)?
Digital Forensics and Incident Response (DFIR) combines the scientific processes for collecting, preserving, and analyzing security incident data with the technical and administrative processes for detecting, investigating, containing, eradicating, and recovering from the incident.
The digital forensics component focuses on:
- Identifying resources for and collecting data about security incidents
- Creating a chain of custody for the original data and making a copy to preserve it
- Analyzing data by manipulating the copy to uncover facts about the security incident
- Reporting the incidents events to law enforcement, lawyers, and senior leadership
The incident response component focuses on:
- Investigating devices, networks, and systems to identify an incident’s root cause
- Containing the incident by isolating affected devices, networks, and systems
- Eradicating the threat actor by removing any malware or other threats
- Restoring assets and systems back to their pre-incident state
DFIR starts with the overlapping investigation and root cause analysis elements, then overlays the controls for evidence preservation so that organizations can use the data in legal proceedings.
How is digital forensics used in the incident response plan?
To contain and eradicate attackers, security teams need to follow the clues that the malicious actors left behind in systems. When collecting and analyzing these clues, the security team often engages in activities associated with various branches of digital forensics:
- File System Analysis: analyzing files systems to identify malicious code
- Memory Analysis: analyzing cache or RAM to identity indicators of attack (IoA)
- Network Analysis: analyzing network traffic patterns to identify attack techniques
- Log Analysis: correlating and analyzing security and event logs to identify suspicious or abnormal activity in environments
These analysis activities are critical to digital forensics. However, they can only be considered forensic evidence when the organization implements appropriate chain of custody and data handling controls.
Why DFIR is important to cybersecurity
Once the organization recovers from the incident, it inevitably works with law enforcement and faces legal issues. For example, companies may need to provide evidence to:
- Law enforcement agencies tasked with tracking down cybercriminals
- Auditors who need to provide reports to regulatory agencies
- Senior leadership who needs to include the data breach in financial reporting
To use the incident response team’s data in these legal proceedings, the organization needs to preserve it according to the rules of evidence. By implementing formal chain of custody processes, the organization ensures that no one tampers with the data, validating the information’s accuracy and authenticity.
By creating a holistic approach to incident response that preserves data, organizations that experience a security incident or data breach have the digital evidence like:
- Identifying how a breach happened and who attackers were
- Prosecuting crimes like fraud, identity theft, embezzlement, or extortion
- Reducing liability during civil lawsuits
What are the primary DFIR challenges?
Digital forensics and incident response are challenging on their own. When you combine them, you multiply the challenges.
Lack of skills
To build a DFIR team, staff need to have cybersecurity and forensic science skills. For example, security analysts need experience with Indicators of Compromise (IoCs) to trace the attack. Additionally, they need to understand the network forensics to connect the IoC to the environment’s network traffic patterns.
Lack of tools
Many companies have a lot of tools, but they may not always have the ones that they need. For DFIR, organizations need tools that enable them to:
- Collect data, including event logs and disk image capture
- Visualize the attack timeline and attacker activity
- Track findings to document activities
- Manage tasks and assign responsible parties
- Correlate similar activities
When companies have disconnected tools, they lack a single source of evidence. Further, organizations need a technology that allows them to track the alert back to its source technology.
Inability to collaborate
Often, security team members will have different experience with the branches of digital forensics. While some members focus on email forensics, others may have experience with IoT or mobile forensics. While gathering and analyzing data, teams need a technology that enables them to collaborate while documenting the chain of custody, including who interacts with the evidence, when they do it, and what actions they take. Without the appropriate tools, the organization won’t be able to use the data in legal proceedings.
DFIR Best Practices
Many organizations outsource DFIR to third-party service providers. However, whether you plan to implement your own DFIR or outsource the activity to a services provider, you can implement some best practices to streamline the process.
Prepare a Plan
You should have an incident response plan that:
- Defines key roles and assigns responsibilities, including incident response managers, security analysts, threat researchers, and internal stakeholders like human resources, public relations, and senior leadership
- Identifies how to manage the data collected so that it can be used as evidence once the organization recovers from the incident
- Sets clear steps for the incident response team to follow
- Outlines reporting requirements
Use High-Fidelity Detection Rules
Responding to an incident starts the moment your security technology detects anomalous behavior.
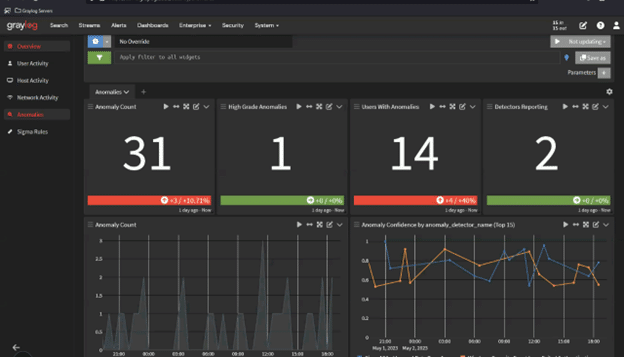
Using high-fidelity detection rules, you reduce alert fatigue and ensure that your security team can prioritize high-impact activities and incidents. For example, you may want to use Sigma rules to detect known attacks while monitoring for unknown attack techniques with alerts that aggregate and correlate activity across:
- User access
- Device configuration
- Applications
- Network traffic
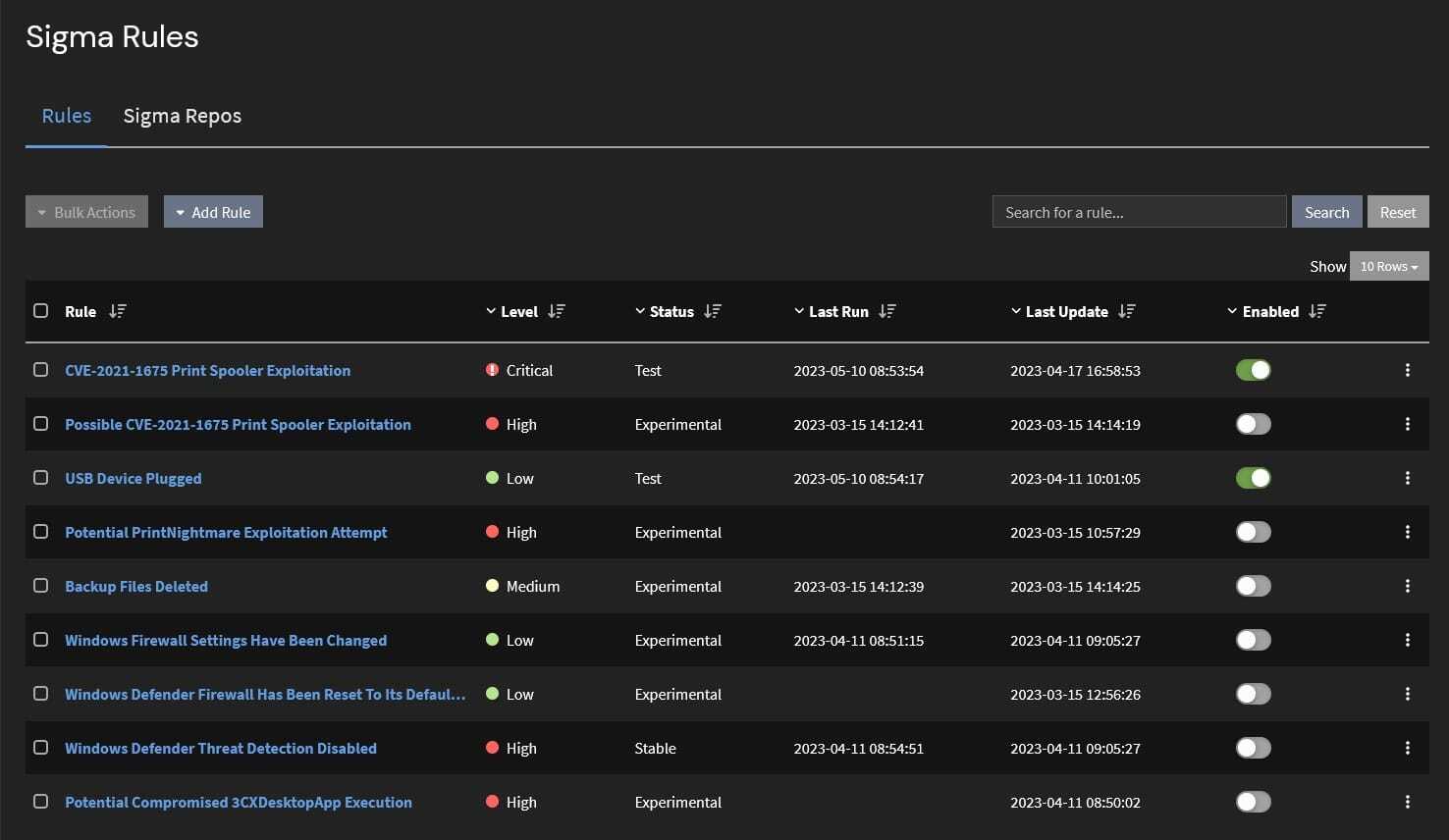
Collect and Analyze Artifacts
As you investigate the incident, you should collect and analyze artifacts like:
- Login sessions
- Operating system data
- Active, modified, or deleted files
- Application data
- Network configurations and connections
- Logs
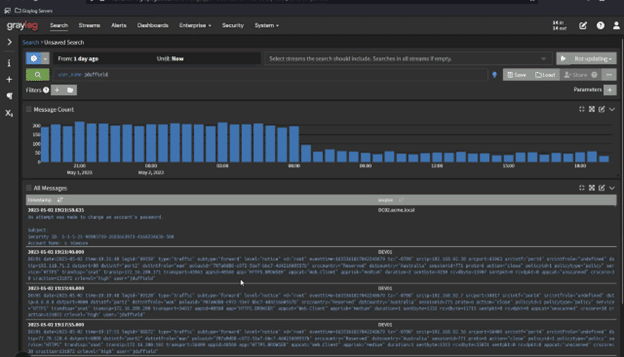
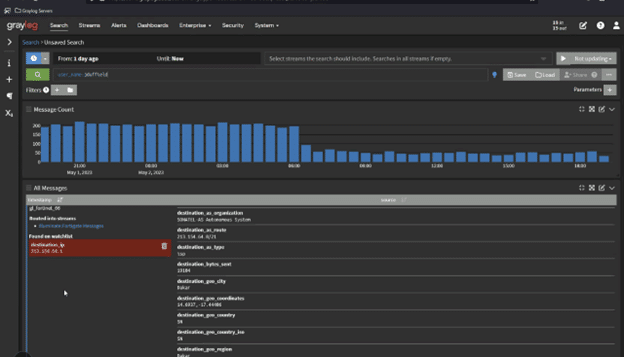
Further, as part of this process, you need process that track the movement and control of the data by documenting:
- Who handled the asset
- Date/time the asset was collected
- Date/time asset was transferred
- Purpose for the transfer
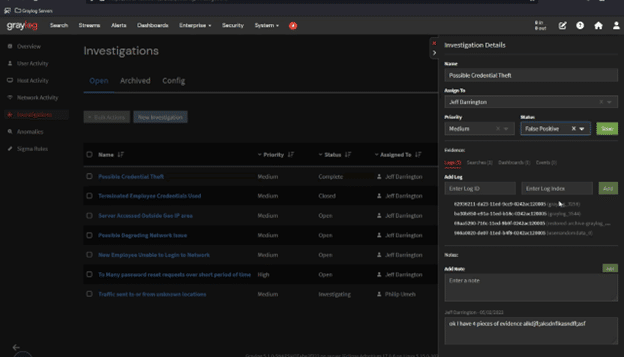
By incorporating these processes into the investigation, you preserve the data’s integrity and prevent contamination.
Contain, Eradicate, Recover
To reduce an incident’s impact, you need to prevent movement, eliminate all malware, and return systems to their pre-incident state, all while preserving evidence. Some best practices include:
- Isolating impacted networks or taking impacts devices offline
- Taking a forensic image of impacted systems
- Remediating issues to bring systems back online
- Wiping and re-imaging impacted system hard drives
- Scanning affected systems for malware to ensure complete removal
- Testing systems to ensure complete eradication and functionality
- Monitoring for abnormal activity
Present and Iterate
Finally, all investigation and forensics need to be reported to the appropriate parties, like senior leadership, law enforcement, or legal teams.
When presenting the forensic evidence, you’re reporting the timeline of events using your data analysis. Your report should consider:
- All plausible explanations when no conclusive evidence exists
- Information each audience needs
- Information that can help prevent future events
Using these reports, your internal team can iterate the security program by:
- Implementing new administrative or technical controls
- Writing more effective alerts
- Identifying additional key performance indicators (KPIs)
Graylog Security: Investigations with Documentation
With Graylog Security, you get the speed, documentation, and accuracy necessary to implement DFIR or support an outsourced DFIR team. Our detections, especially our Sigma rules, enable you to detect and investigate incidents by giving you the keywords necessary to trace known attack types. Within Security Investigation, you can create a new case, create custom prioritizations, document status, assign responsible incident responders, report findings, and link to log data evidence.
By leveraging Graylog Security’s out-of-the-box content and security analytics, you can build high-fidelity alerts then pivot directly into researching the log data that matters most. Our platform gives you all the functionality of a SIEM without the complexity, providing a robust technology that empowers users of all experience levels.
To see how Graylog Security enables your digital forensics investigations goals, contact us today.



