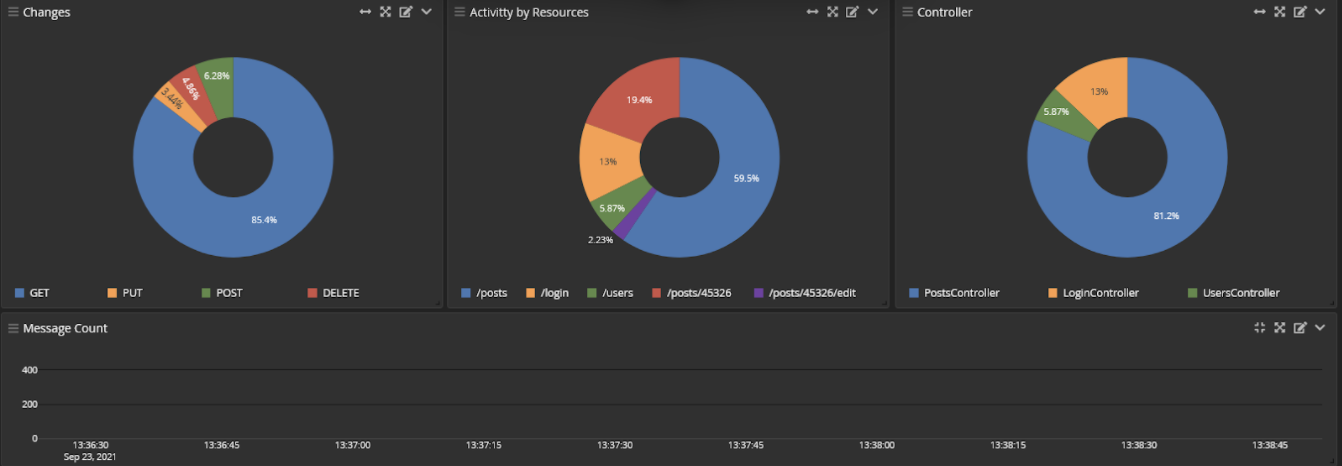
Graylog’s log aggregation and analysis capabilities are applicable to far more than just security. They can create new value in almost every business process or technical domain organizations want to








We’ve discovered that the Graylog RPM packages contained a blank systemd unit file. As a result, we have pulled these two releases. If you have already upgraded your Graylog platform
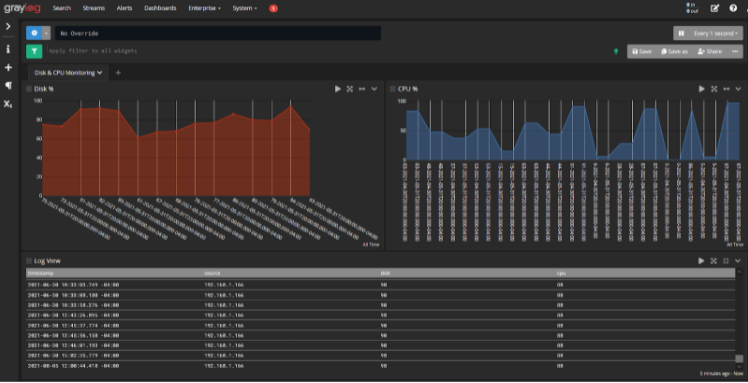

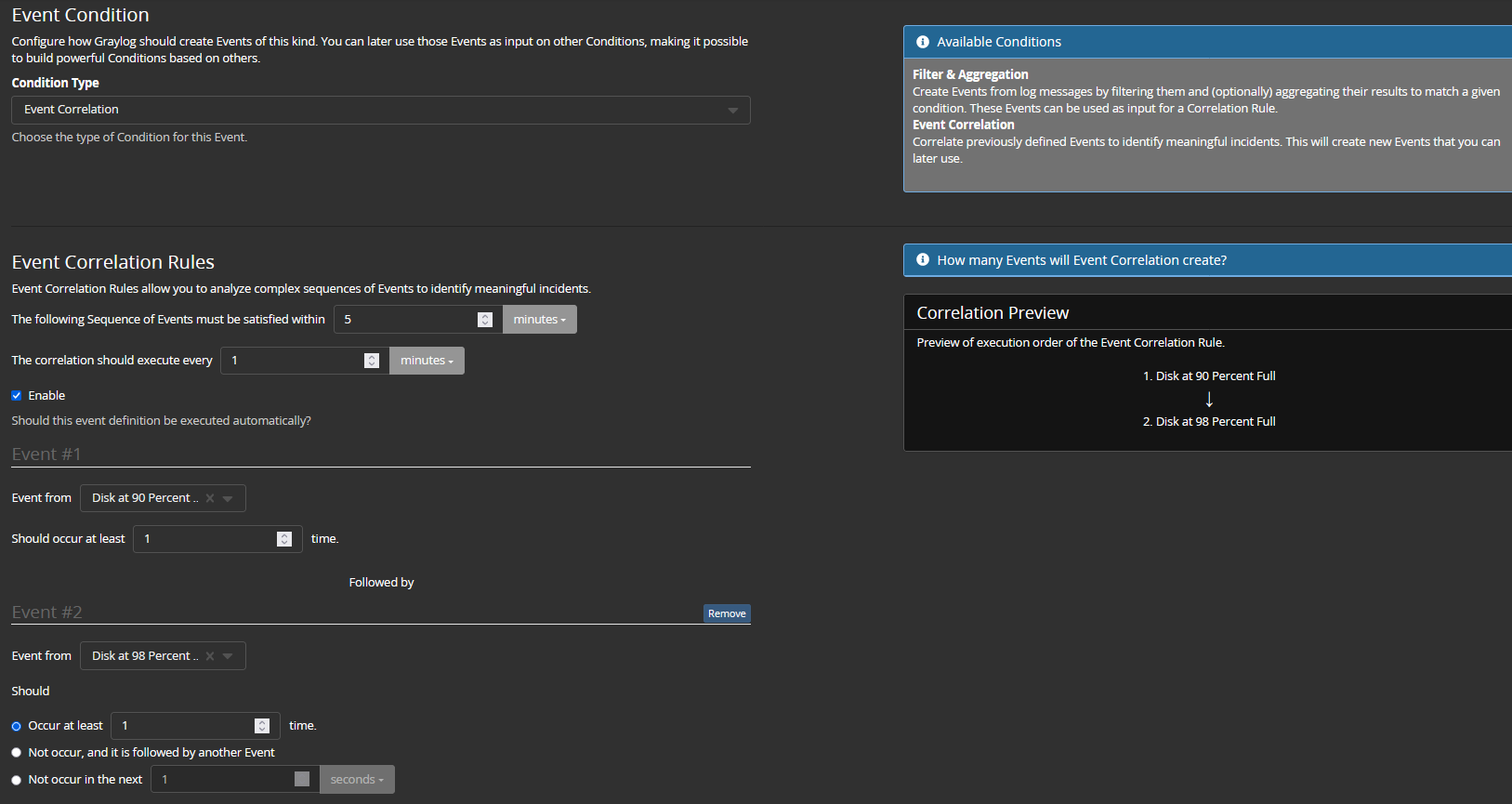


Products
Follow Us:
© 2024 Graylog, Inc. All rights reserved