Graylog API Security
The Ultimate Solution for End-to-End API Threat Monitoring, Detection, and Response
APIs are a vital component of internet traffic and business continuity, serving as gateways to software applications and often exposing a portion of a business’s internal functions to the external world. In today’s interconnected digital ecosystem, cyberattacks are becoming more sophisticated, making APIs more vulnerable to attacks if not properly secured.
APIs are under attack
70%
of API traffic is malicious
APIs are unknown
1/2
of APIs are unmanaged
Limited API skills
#1
API security concern is lack of expertise
Elevate Your API Security
Beyond Traditional Defenses
In an era where cyber attackers can cleverly disguise themselves as legitimate users, traditional firewalls and gateways are no longer sufficient. Secure your digital ecosystem against sophisticated threats with our advanced API security solution, tailored to meet the complexities of modern cyber warfare.
Why Standard WAFs Aren't Enough:
- Specialized API Protocols and Data Formats: Standard WAFs are fluent in HTTP/HTTPS, but when it comes to the unique dialects of APIs – like SOAP, XML-RPC, gRPC, not to mention data formats like JSON and XML – they are often lost in translation. These custom formats demand specialized parsing and validation, something beyond a typical WAF.
- Enhanced Visibility into Encrypted Traffic: WAFs can peek into encrypted traffic, but newer or more complex encryption algorithms are like lead walls to their x-ray vision. Since APIs often employ robust encryption, this severely limits the WAF’s ability to scrutinize API calls effectively.
- Sophisticated Rate Limiting and Abuse Detection: While WAFs can perform some level of rate limiting and abuse detection, APIs call for a more nuanced approach. This includes understanding the user, the application state, and the specific API endpoint – a level of discernment typically beyond the reach of standard WAFs.
- Agile Adaptation to API Evolution: APIs constantly evolve, introducing new versions and altering the attack surface. WAFs struggle to keep pace without extensive manual configuration and tuning.
- Protection Against Zero-Day Exploits: WAFs and other perimeter-based API Security tools rely on known patterns and signatures to detect attacks. But in the world of APIs, the unknown lurks around every corner in the form of zero-day exploits and new vulnerabilities, often slipping past WAF defenses unnoticed.
- Targeted Defense Against API-Specific Attacks: Certain attacks are tailor-made for APIs, such as parameter pollution, IDOR (Insecure Direct Object References), and complex injection attacks. These require more advanced detection mechanisms than what a typical WAF can offer.
API Security Done Right with Graylog
Graylog API Security is a self-managed/on-premise solution designed to be a trusted guardian while offering unparalleled end-to-end protection for your most business-critical APIs. Our solution isn’t just another layer of security – it’s a smarter, more adaptable shield designed to protect your APIs against the most cunning and elusive threats. Ensure the safety of your digital assets with our state-of-the-art API security technology.
“How many APIs does your organization have?”
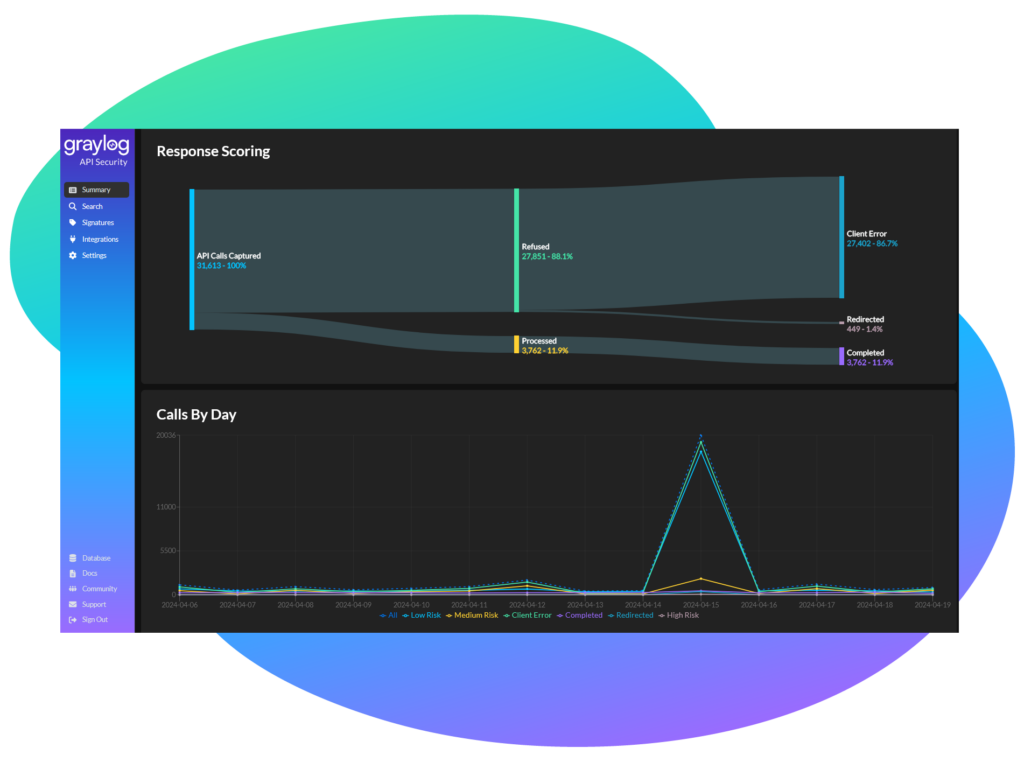
This is a sobering question most CISOs aren’t able to answer because, simply put, they do not know, so creating a comprehensive API security strategy is almost impossible to accomplish. Graylog API Security helps answer this question with Continuous API Discovery, tirelessly scanning all API traffic at runtime for proactive discovery while categorizing your API calls and ensuring nothing escapes notice. Incoming traffic is sorted into domain buckets based on your top-level domain. Combining discovery with automated risk assessment scoring capabilities allows Graylog API Security to provide a 2-pronged approach to TDIR, bridging the communication gap between DevOps and Security teams so they can work in concert to identify potential issues and devise informed remediation strategies.
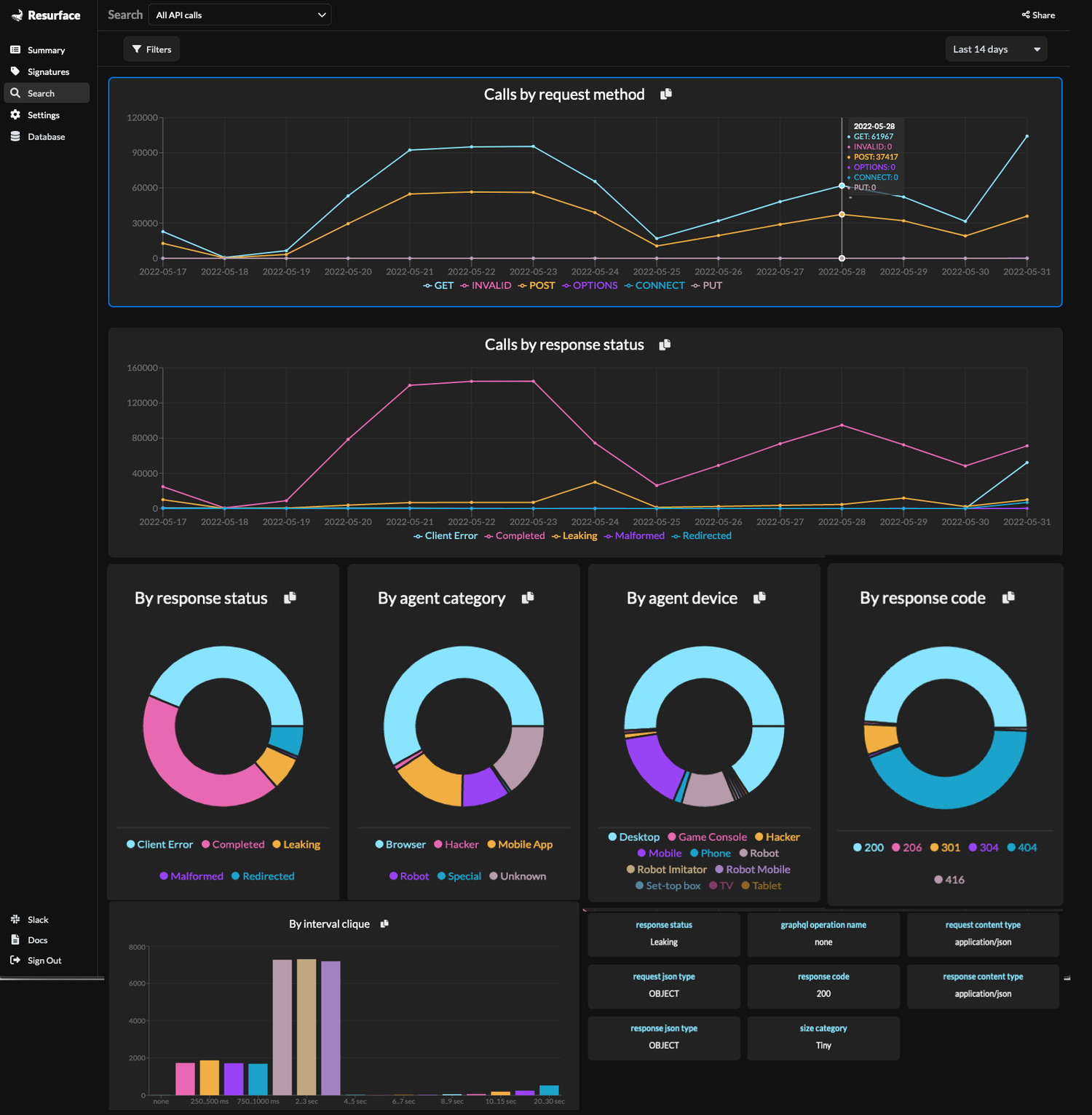
Full API Request & Response Capture: The Unfiltered Truth
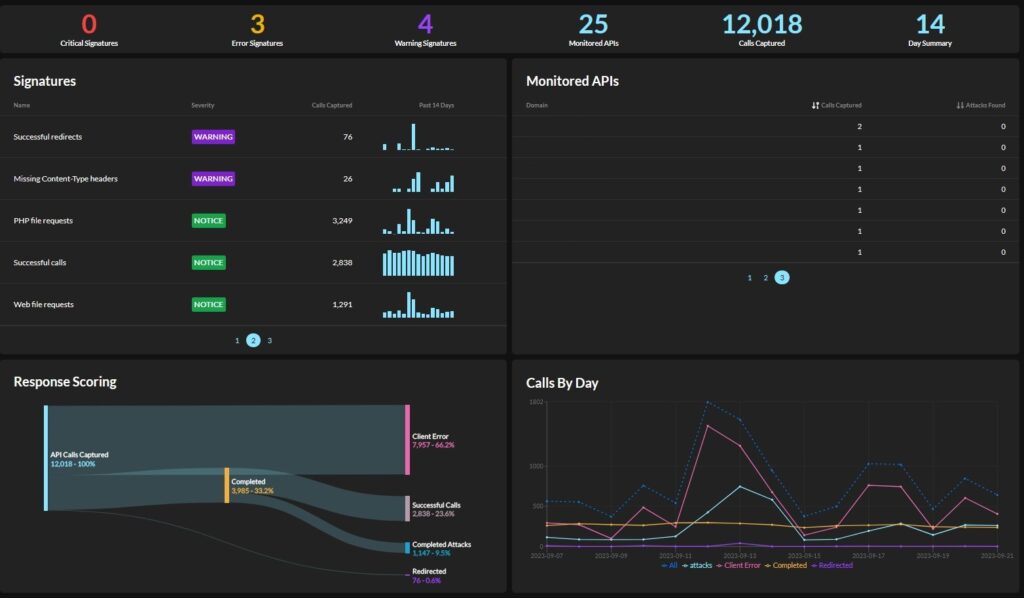
The journey continues as Graylog API Security is the only solution that captures and stitches together the unfiltered API request with response details, enhanced with runtime analysis, creating a readily accessible datastore for attack detection to identify common threats and API failures swiftly and accurately by using Integrated Threat Signatures aligned with OWASP and MITRE guidance to help you reduce operational metrics like Mean Time to Detect (MTTD). Graylog API Security also powers threat intelligence with a hot data layer for immediate retroactive analysis, allowing your teams to detect zero-day issues and search all API calls retroactively to identify patterns and track actions.
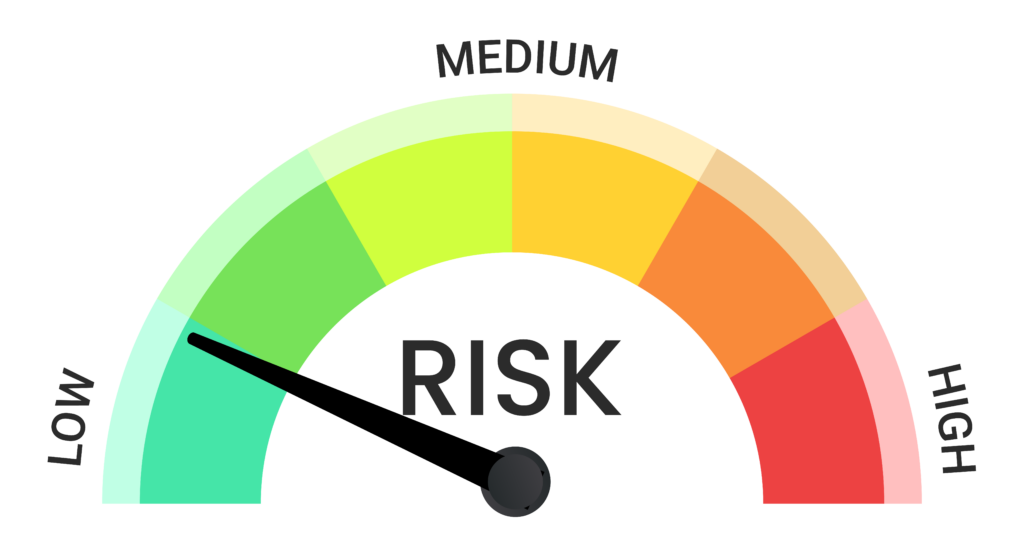
Tuned Risk Assessment Scoring:
A Game-changer in Graylog API Security
Graylog API Security doesn’t just alert you on potential vulnerabilities; it empowers your Security and DevOps teams with Automatic Risk Assessment Scoring that is tuned to the type of API being monitored (REST, GraphQL, JSON) and highlights high-risk areas that need immediate attention with precision.

Graylog API Security:
Actionable Solutions and Remediation Tips
Graylog API Security doesn’t just stop at detection. Every raised alert includes:
- A summary of the underlying security issue along with a high-level histogram for immediate context regarding the activity and intensity.
- Automatic remediation guidance and actionable insight to help quickly resolve issues and optimize critical metrics like Mean Time to Respond (MTTR).
- Customizable remediation guidance options to help Security and DevOps teams meet goals within their collaboration tool of choice.
- "Learn more” options for each alert that connect directly to the Graylog Console for additional alert context and situational awareness, enabling fast and effective decision-making as teams respond to specific security situations.
Graylog API Security
Graylog API Security is not just another security tool. It is a comprehensive, end-to-end story of robust API discovery, threat detection, and incident response (TDIR), ensuring your digital assets are safeguarded at every step. Choose Graylog API Security, where security is not just a promise.
USE CASE
Financial Services
Broken Object Level Authorization (BOLA), API parameter tampering, session hijacking, and other exploit types.
Graylog API Security continuously scans all request and response payloads from every endpoint in real time, giving you the data necessary to understand and expose potentially malicious traffic. Using these complete datasets, you can uncover, triage, and retroactively assess API anomalies like unchecked access for user IDs, unvalidated URL parameters, and missing HTTPS in sessions.
USE CASE
Technology
Hard-coded API keys, deprecated APIs still accessible, object-level authorization.
Graylog API Security continuously scans all request and response payloads from every endpoint in real-time, supporting your cybersecurity program with data on potentially malicious traffic in development, production, and retroactive assessment. Using these datasets, security teams uncover and mitigate insecure API coding practices, insufficient parameter validation, unusual traffic patterns, and more.
Interested in API Security?
Cloud Providers



Container Environments


API Gateways




Reverse Proxies


Microservice Frameworks







API Clients

Get the Monthly Tech Blog Roundup
Subscribe to the latest in log management, security, and all things Graylog blog delivered to your inbox once a month.