It’s been a week. A long week. After the most recent Board of Directors meeting, your senior leadership tasked you with finding a security analytics solution. Over the last month, you’ve worked with leadership to develop some basic use cases to determine which solution meets your security and budget needs.
You started your research, but everything on the market seems really overwhelming. The Security Information and Event Management (SIEM) tools have the capabilities you want – and then some. It’s expensive and, frankly, more power than you need right now.
You’re looking at a deployment time of at least six months, and you don’t have that much time. Worse, the specialized query language means you’ll need to train your team, adding to the timeline.
On the other hand, everyone already knows how to use your centralized log management tool. With the right planning, you can use your centralized log management solution to get the security intelligence analytics you need and increase your return on investment.
WHAT IS SECURITY INTELLIGENCE?
You want a security analytics tool, but you’re not sure what security intelligence actually is.
Security intelligence gives you visibility that reduces risks with insights that allow you to make informed-decisions. It includes real-time collection, normalization, correlation, and analysis of all data that users, applications, and environments generate.
If you’re thinking “that definition sounds a lot like centralized log management,” you’re right. It does. The right solution can get you exactly what you need without all the additional costs associated with a SIEM.
WHAT ARE THE MAJOR ELEMENTS OF SECURITY INTELLIGENCE?
Your centralized log management solution already aggregates, parses, normalizes, correlates, and analyzes event logs from across your environment.
INGESTING DATA IN REAL-TIME
Your log management solution does this all day, every day. Your IT team already uses your log management tool to rapidly investigate help desk tickets. Since every technology also includes security event logs, you can use centralized log management for security.
PARSING, NORMALIZING, CORRELATING, AND ANALYZING DATA
Centralized log management tools exist, in large part, to give IT teams a way to use their event logs effectively. One of their core functions is to parse, normalize, correlate, and analyze the data. When they ingest security event logs from across the environment, they become security intelligence tools. If your centralized log management solution has a robust correlation engine, you’re getting the data analytics you need for threat detection.
USING THREAT INTELLIGENCE
Often, the “intelligence” part of security intelligence comes from bringing in additional data sources. With threat intelligence, security teams can integrate information about cyber threats into their monitoring to transform a centralized log management tool into a security intelligence solution.
ENRICHING DATA FOR HIGH FIDELITY ALERTS
When you’re able to bring all this security data together in a single location, you get better alerts that generate fewer false positives. Now, your team is able to detect, investigate, and resolve threats more rapidly within a tool they already know how to use.

PLANNING YOUR LOG MANAGEMENT DATA COLLECTION STRATEGY FOR SECURITY INTELLIGENCE ANALYTICS
When you add big data analytics, like machine learning, to your security intelligence tool, you get security intelligence analytics. Centralized log management solutions can do this, too. If you plan your log collection effectively, then you can do more with the tool you already have.
SECURITY
To mature your security posture, you need pre-incident and post-incident visibility and documentation. Your centralized log management solution when coupled with data analytics provides this. When you collect and archive security logs, you’re able to detect abnormal activity faster, investigate effectively, and review forensic data after remediating issues.
When you start planning your log collection strategy for a security analytics use case, you should consider the following sources and types of data:
- Anti-Virus tools
- Endpoint Detection and Response (EDR)
- Server logs
- Firewall logs
- Network traffic
- Web proxies/Gateways
- Intrusion Detection Systems (IDS)/Intrusion Prevention Systems (IPS)
- Identity and Access Management (IAM)
- User behavior
- Threat intelligence feeds
DEVOPS
Maturing your security posture means including your DevOps team in the process. Shifting security left by securing the Software Development Lifecycle (SDLC) means reviewing code and managing security after pushing the application to production.
As you plan your log collection strategy, you should consider the following sources and types of data:
- Application logs
- Load balancer logs
- Automation system logs
- Business logic data
- User logs
- Network activity
- Database logs

COMPLIANCE
Just as you can use your centralized log management solution to monitor activity and investigate incidents, you can use it for compliance reporting. Your senior leadership is pushing for a security intelligence analytics tool because they need to understand the company’s risk posture to meet compliance mandates.
Using your centralized log management tool for security analytics gives you the ability to do this. You can create visualizations that provide high-level visibility into your security posture. With automation, you can send these reports on a regular schedule without having to remember to pull the data all over again.
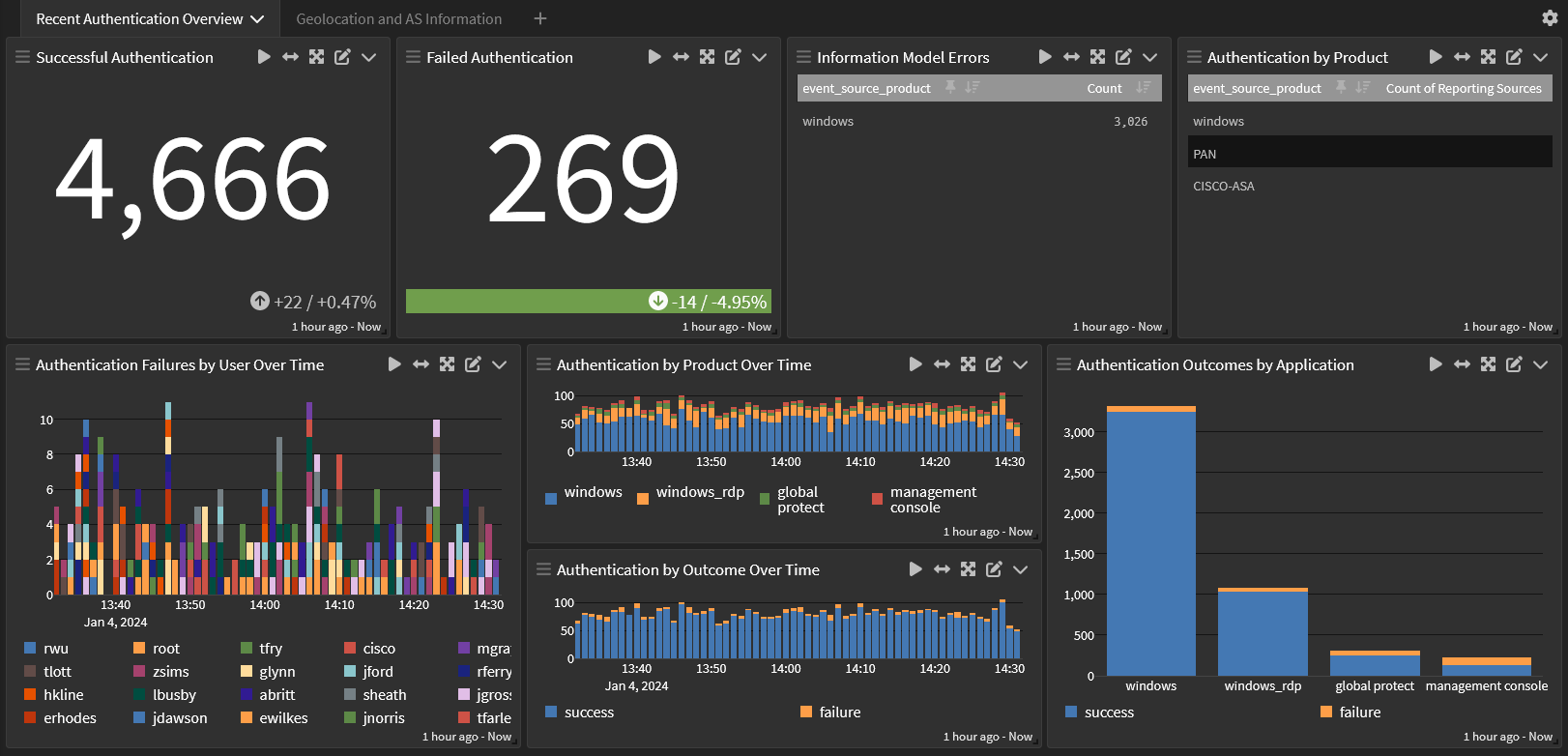
For example, a dashboard that shows trends over time can provide visibility into how well the organization manages its security posture.
GRAYLOG: SECURITY INTELLIGENCE ANALYTICS FOR BETTER RETURN ON INVESTMENT
With Graylog Security, you can get the security analytics you need without the high cost – both in time and money – that comes with a SIEM. Most IT teams already know how to use a centralized log management tool so they can use the skills they have to mature your security posture.
Graylog gives you a two-in-one solution that works across security and IT operations for increased return on investment. With our high fidelity alerts, you reduce Mean Time to Detect. Meanwhile, our lightning-fast search capabilities reduce Mean Time to Investigate and Mean Time to Recover.
Maturing your security posture doesn’t have to be cost prohibitive. With Graylog as your extra set of hands, you get the capabilities you need without the extras that you don’t want.

















