It was just another day in paradise. Well, it was as close to paradise as working in IT can be. Then, your boss read about another data breach and started asking questions about how well you’re managing security. Unfortunately, while you know you’re doing the day-to-day work, your documentation has fallen by the wayside. As much as people are loathed to admit it, this is where compliance can help. By understanding the intersection between centralized log management and the NIST Cybersecurity Framework (CSF), you can prove your security posture with the necessary documentation.
WHAT IS THE NIST CYBERSECURITY FRAMEWORK (CSF)?
The National Institute of Standards and Technology (NIST) updated its CSF in 2018. The NIST CSF takes a risk-based approach to cybersecurity setting out five core functions (Framework Core):
- Identify: Analyze risks arising from users, devices, networks, data, and systems
- Protect: Implement technical controls for mitigating identified risks
- Detect: Implement processes for continuous monitoring to detect anomalies and security events
- Respond: Implement incident response processes for communication, analysis, mitigation, and improvements
- Recover: Implement recovery planning processes that include improvements and communications
WHY CHOOSE NIST CSF?
NIST CSF is a popular framework because its risk-based approach gives you a lot of flexibility. It outlines a set of best practices and gives you a way to create controls that respond to your unique risk profile.
A MATURITY MODEL
The Framework Implementation Tiers (Tiers) give you a roadmap for defining and iterating your security maturity. You can start with the Tier that best describes your current security posture, then start working toward processes and documentation that help you move through additional Tiers.
NIST CSF DEFINES THE FOLLOWING:
Tier 1: Partial:
- No formalized risk management process
- Limited risk management capabilities
- Generally unaware of supply chain risks
Tier 2: Risk Informed:
- Risk management practices approved by management but not established as organization-wide policies
- Risk management awareness at organizational level but no established organization-wide management approach
- Aware of supply chain risks but not consistently or formally mitigating them
Tier 3: Repeatable
- Risk management practices formalized and expressed as policy
- Organization-wise integrated cybersecurity risk management approach implemented through risk-informed policies, processes, and procedures
- Aware of supply chain risks and acts on them using contracts and policies
Tier 4: Adaptive
- Risk management practiced formally approved, expressed as policy, and regularly updated to respond to new risks
- Organization-wide cybersecurity risk management approach using risk-informed policies, processes, and procedures that are aligned to organization objectives
- Understands and consistently acts upon supply chain risks using real-time or near-real-time information
STEPS FOR MATURING CYBERSECURITY
Another reason you might want to follow the NIST CSF is that it gives you a series of steps to take and repeat as you move through the different Tiers.
- Step 1 – Prioritize and Scope: Determine business goals and set scope of systems for each business line or process to set risk tolerance
- Step 2 – Orient: Identify all systems, assets, and regulatory requirements for setting risk approach
- Step 3 – Create a Current Profile: Map current controls to Framework Core
- Step 4- Conduct Risk Assessment: Analyze likelihood and impact of a cybersecurity event as well as emerging risks
- Step 5 – Create a Target Profile: Set out desired cybersecurity outcomes to reflect criteria within target Implementation Tier
- Step 6 – Determine, Analyze, and Prioritize Gaps: Create prioritized action plan to achieve outcomes detailed in Target Profile
- Step 7 – Implement Action Plan: Define actions to address gaps and adjust practices to achieve Target Profile
WHAT REGULATIONS OR STANDARDS MAP TO NIST CSF?
The even better news about the NIST CSF is that it maps to many regulations and other standards.
For example, the following industry standards have similar controls and processes that NIST CSF can help you with:
- International Organization for Standardization (ISO) 27000-series
- Center for Internet Security (CIS) Controls
- System and Organization Controls (SOC) Trust Services Criteria (TSC)
- North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) Reliability Standards
- NIST Special Publication (SP) 800-171
- Control Objectives for Information and Related Technology (COBIT)
- American National Standards Institute/International Society of Automation (ANSI/ISA)
Additionally, NIST CSF can be used as a starting point to meet regulatory requirements like:
- Health Insurance Availability and Portability Act (HIPAA)
- General Data Protection Regulation (GDPR)
- Sarbanes-Oxley Act (SOX)
- Gramm-Leach-Bliley Act (GLBA)
- Cybersecurity Maturity Model Certification (CMMC)
Once you get your NIST CSF compliance documented, you can look for gaps with other standards or regulations. The flexibility of NIST CSF makes it useful when you have to respond to vendor due diligence questionnaires from prospective customers who may have different compliance needs.
WHY IS NIST CSF COMPLIANCE DIFFICULT?
From a bird’s eye view, NIST CSF might seem easy. It’s only five Framework Core functions. Once you dive in, you can start to see why people might groan at the thought of going down this road.
Each of the five main Framework Core functions is a list of Categories. Each category is then broken into multiple Sub-Categories. Within those Sub-Categories, you just have a single line of text with no concrete technical guidance.
Each Sub-Category then has a list of “Informative References.” These are great because they can help you get a sense of what to do to set a control for the Sub-Category. However, the standards in the Informative References keep changing from one Sub-Category to the next.
Let’s take a quick look at two Sub-Categories in the first Category “Asset Management,” under the first Framework Core function and their Informative References:
- ID.AM-1: Physical devices and systems within the organization are inventoried
- CIS CSC 1
- COBIT 5BAI09.01, BAI09.02
- ISA 62443-2-1:2009 4.2.3.4
- ISA 62443-3-3:2013 SR 7.8
- ISO/IEC 27001:2013 A.8.1.1, A.8.1.2
- NIST SP 800-53 Rev. 4 CM-8, PM-5
- ID.AM-4: External information systems are cataloged
- CIS CSC 12
- COBIT 5 APO02.02, APO10.04, DSS01.02
- ISO/IEC 27001:2013 A.11.2.6
- NIST SP 800-53 Rev. 4 AC-20, SA-9
Ok, so in these two subcategories, you have a few different challenges:
- ID.AM-4 doesn’t reference the ISA standards
- Both CIS and NIST SP 800-53 have been updated since 2018
- You either need to choose one informative reference or look at all sixteen listed reference points for two controls.
In other words, it’s just not as easy as “risk-based framework for flexibility” might sound.
WHERE DOES LOG MANAGEMENT FIT INTO NIST CSF COMPLIANCE?
If getting compliant wasn’t hard enough, you have to stay compliant. They say the devil is in the details, and event logs are the details that aren’t devils.
To stay compliant, you need documentation. Event logs, audit logs, and log files contain data showing all activities happening across your environment. Each user, device, network, and system generates log data.
Admittedly, that’s even more overwhelming, especially when you have an on-premises, multi-cloud, and hybrid environment that can generate terabytes of log data per day.
This is where the magic of centralized log management can help. Centralized log management gives you a single location for collecting, aggregating, correlating, and analyzing all your event logs so that you can make sense of your data and document everything happening in these complex environments.
PROTECT: PR-PT-1
The first Sub-Category under Positive Technology (PR-PT) states:
Audit/log records are determined, documented, implemented, and reviewed in accordance with policy.
In other words, you need audit logs for everything and need to review them. Centralized log management gives you that single source of visibility and documentation.
PROTECT: PR-AC-4
Identity Management, Authentication, and Access Control (PR-AC) also give you insight into how you can use centralized log management for NIST CSF compliance. This control states:
Access permissions and authorizations are managed, incorporating the principles of least privilege and separation of duties.
As traditional network boundaries disappear, access management is fundamental to security and compliance. It’s also really difficult, especially as people request new access or move within the company.
This is when you can use log management to track and monitor user activities to document that you have controls and that they’re working.



PROTECT: PR-AC-2
This control states:
Physical access to assets is managed and protected.
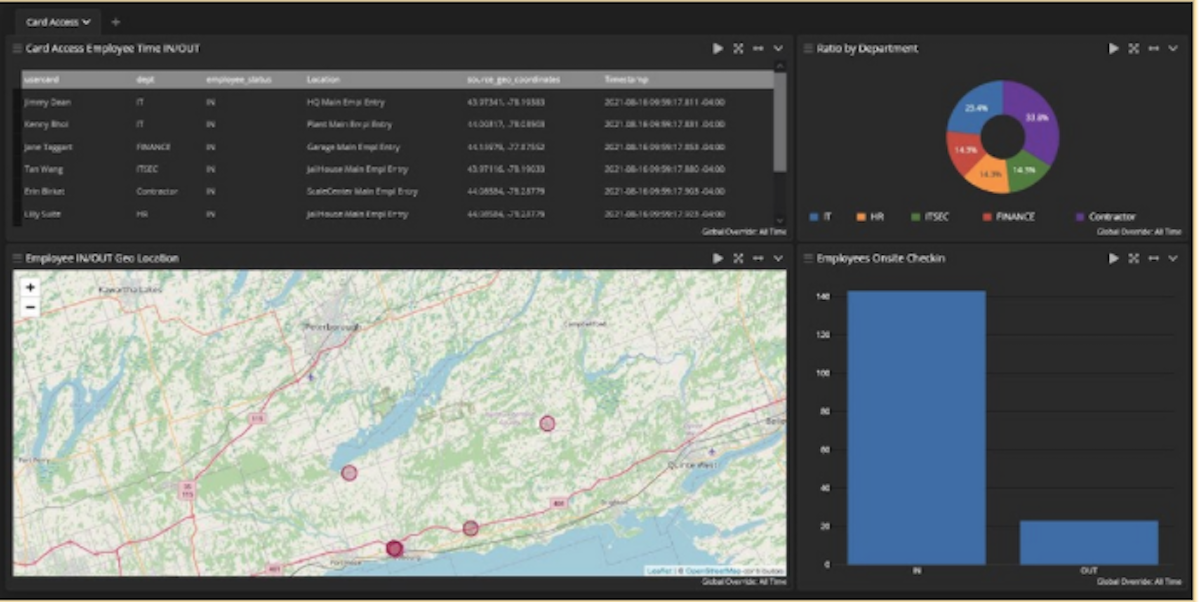
You might be thinking that centralized log management is only for digital assets. While that’s true, you’re also probably using digital assets to help manage physical access and security. A lot of companies use cards to give employees access to buildings, and yes, centralized log management can help manage the monitoring of this.

DETECT: DE.CM-1
Under the Detect function, you need to meet the Security Continuous Monitoring (DE.CM) Category Requirements. Subcategory DE-CM-1 states:
The network is monitored to detect potential cybersecurity events.
Well, that’s a bit vague, but centralized log management is built to help you detect abnormal network traffic.

DETECT: DE.CM-4
With malware and ransomware on the rise, DE.CM-4 is more important than ever. This Sub-Category states:
Malicious code is detected.
NIST CSF is a compliance mandate of few words. It’s not enough to just put anti-virus software on devices, even though it’s really important. You also need a way to detect malicious code as part of endpoint security.
Centralized log management can help here. Once you ingest your security log data, you’re able to create events that trigger high-fidelity alerts. It’s even more useful if you’re able to incorporate threat intelligence that helps you keep up-to-date with the most recent attack types.


RECOVER: RC.CO-3
Under the Recovery function, the Communications Category includes this Sub-Category which states:
Recovery activities are communicated to internal and external stakeholders and executive and management teams.
Sometimes, communicating your activities to non-technical people is difficult as a technology person. Your executive and management teams need visibility into whether you’ve recovered from a security incident and need to understand to fulfill their roles.
If you’re using Dashboards in your centralized log management tool, you can show trends over time using visualizations like charts and graphs if you include the before, during, and after, you can show your remediation and recovery processes.
GRAYLOG FOR NIST CSF
Graylog gives you the centralized log management solution that helps you get compliant – and stay that way. We make it easy to visualize and explore data so that you can document your NIST CSF compliance activities. You can flag people and/or assets based on compliance requirements to not spend as much time on reporting.