
- February 6, 2023
Proactive Event Notifications Proactive event notification is one of the most valuable components of centralized log management and SIEM. It allows us to identify problems, misconfigurations, and potential security risks

Proactive Event Notifications Proactive event notification is one of the most valuable components of centralized log management and SIEM. It allows us to identify problems, misconfigurations, and potential security risks
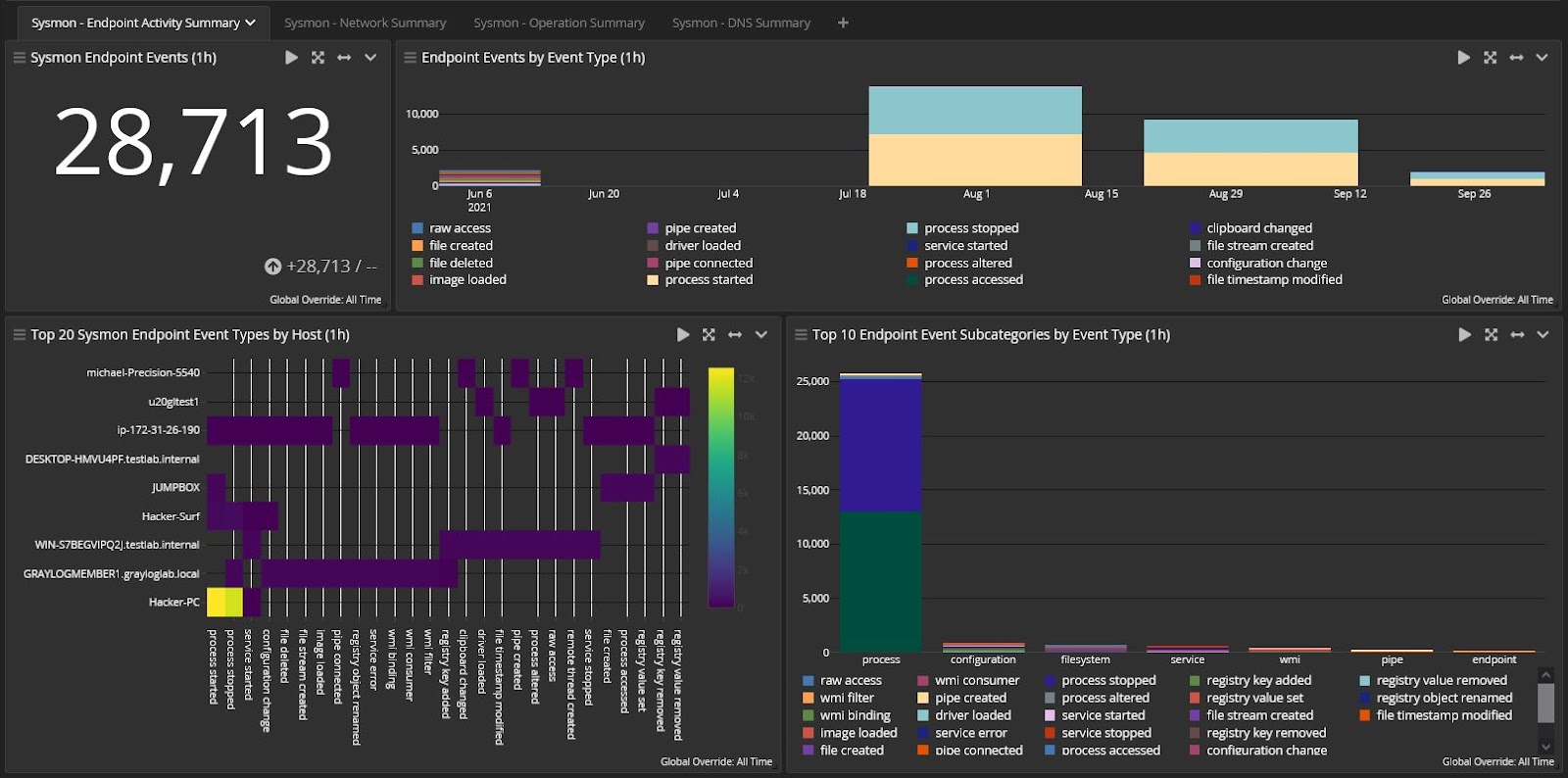

If your company is like many others, it probably invested heavily in the Microsoft ecosystem. Microsoft has been around since the 1980s, focusing primarily on business technologies. It has a

If you’ve ever seen Indiana Jones and the Last Crusade, you might remember the scene where Indy and his dad are in a room replete with the most ornate chalices
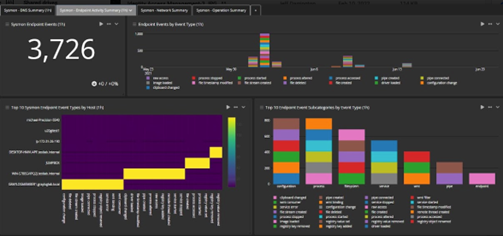
For today’s remote workforce, security professionals need technical security awareness education distinct from the rest of the company’s “don’t click a phishing link” training. Security analysts know how to recognize
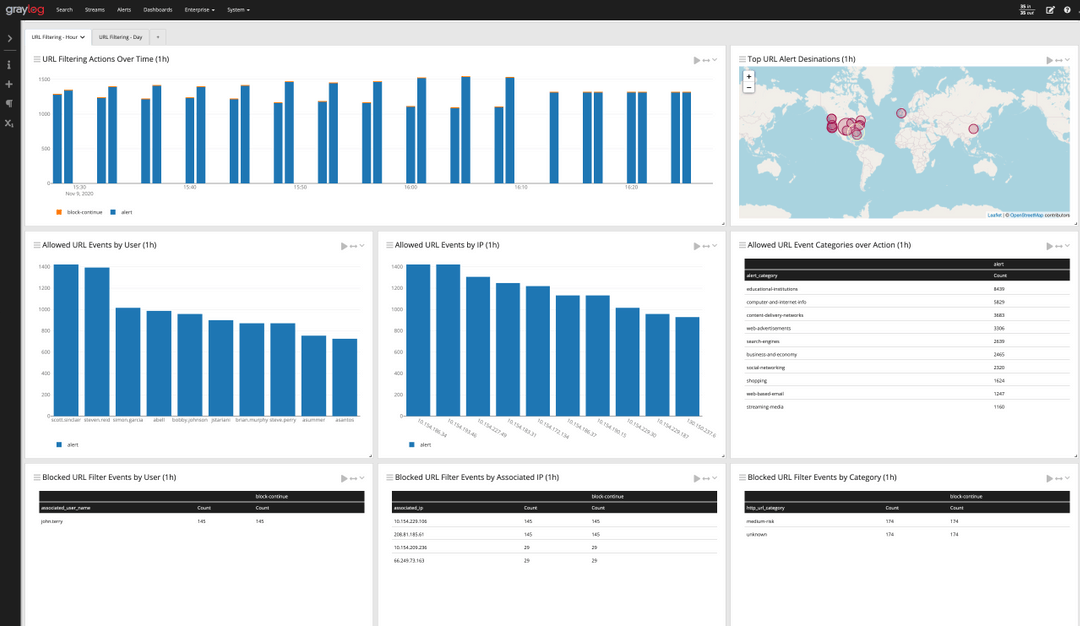
As an IT service manager, you love solving problems and helping your people improve business processes. You thrive on those unexpected moments where your experience adds value, whether providing advice

When working with log messages, the log message’s timestamp must be accurate. Some problems that incorrect timestamps create include: Difficulty searching for log messages based on specific date/time Alerts not
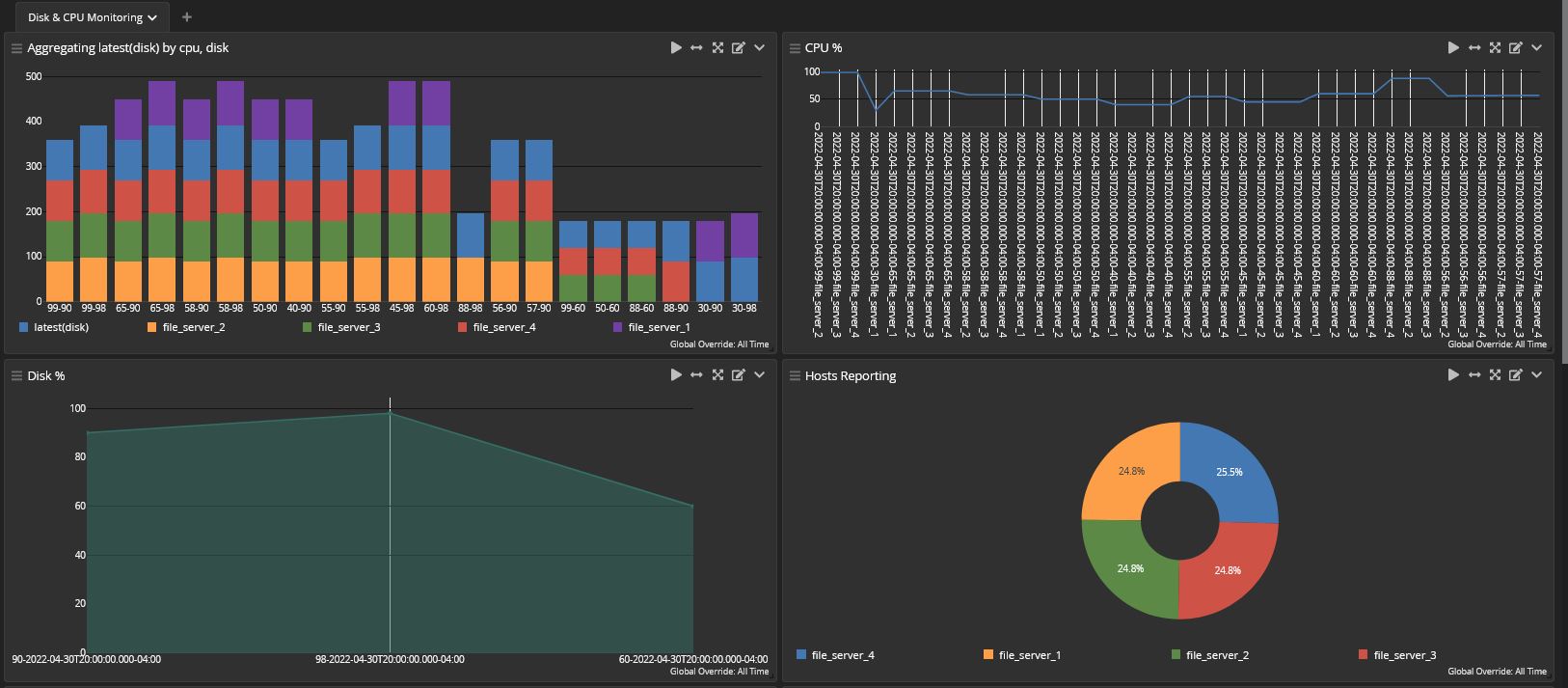
The financial services industry has been a threat actor target since before digital transformation was even a term. Further, the financial services organizations find themselves continuously under scrutiny. As members
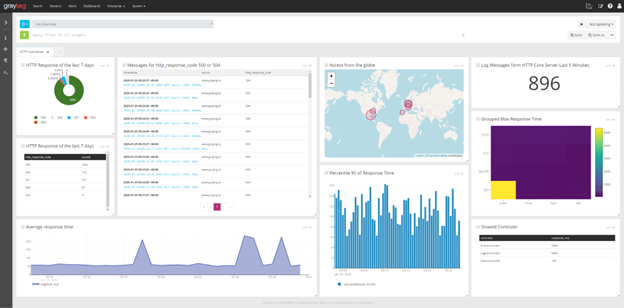
Another day starting up your laptop or workstation, logging into programs, and waiting for that first call to come in. As an IT help desk analyst, you love when you
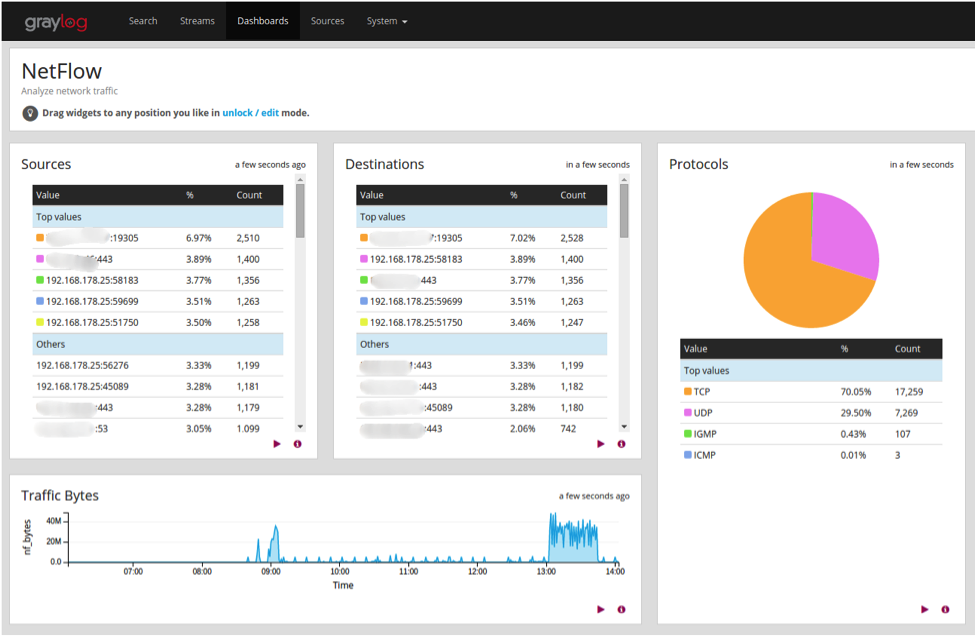
When the world went remote in March 2020, cloud technologies made work possible. Rapid digital transformation changed everyone’s jobs, whether in-office, remote, or hybrid. Today, your business relies on network
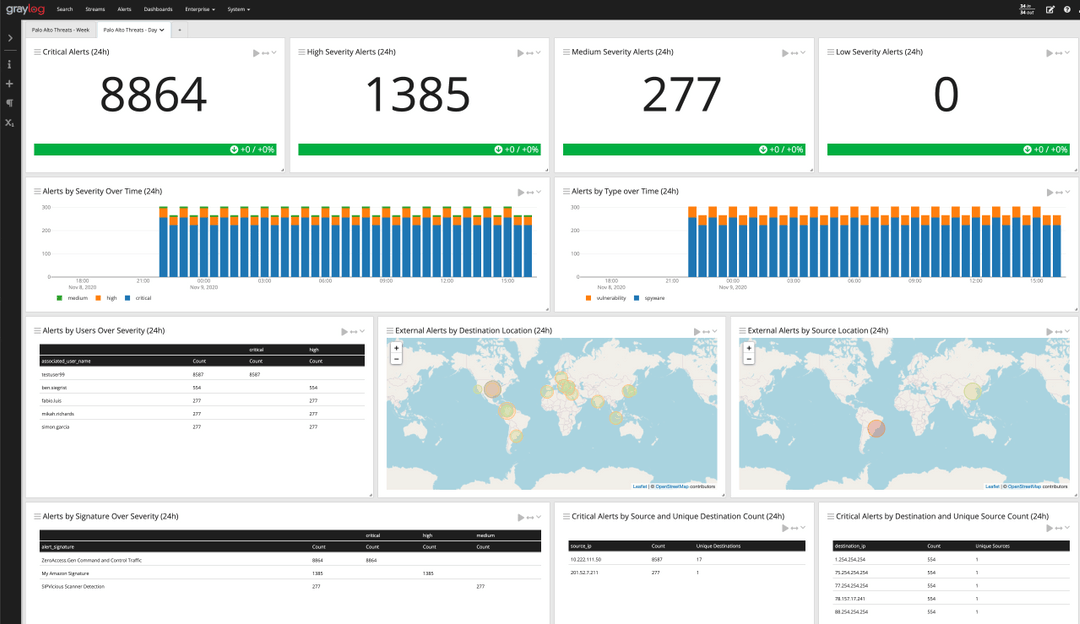
Governments, businesses, and society depend on reliable, functioning information and communication technology. However, increased severity of ransomware attacks and vulnerabilities in computer chips undermine these infrastructures. Further, as people adopt

Many organizations today have strict data privacy regulations that they must comply with. These privacy regulations can often clash with the requirements of security, application and operations teams who need
Follow Us:
© 2024 Graylog, Inc. All rights reserved