
Log Management and Graylog Alerts – Keeping Track of Events in Real-Time
Alerts are a critical component of every log management solution. Graylog alerts are incredibly accessible and they provide the information you need in real-time.
Security, availability, and performance were the focus for companies navigating the changing workspace in 2020. As a holiday treat, each day, Graylog will present you with the blog posts, videos, and recorded webinars that our website visitors looked at for guidance on how to keep their IT infrastructure secure, available, and optimized.

Alerts are a critical component of every log management solution. Graylog alerts are incredibly accessible and they provide the information you need in real-time.

As companies responded to the COVID-19 pandemic with remote work, cybercriminals increased their social engineering and ransomware attack methodologies. Ransomware, malicious code that automatically downloads to a user’s device and locks it from further use, has been rampant since the beginning of March 2020. Detection of ransomware through log management offers one way for you to protect your systems, networks, devices, and applications for continued data security.
What role does log monitoring have in intrusion detection and prevention and how does it work together with behavioral analytics?
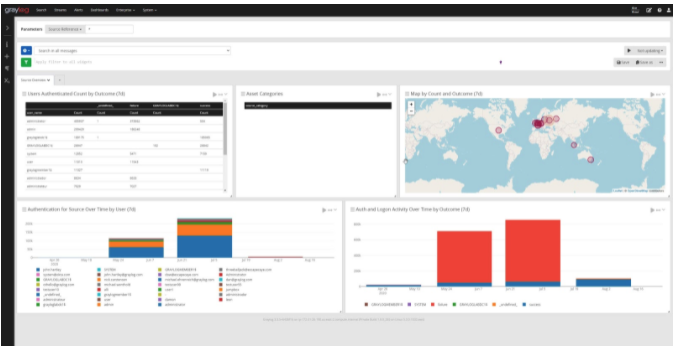
Log management is important to cybersecurity because it provides the data needed to detect, investigate, and respond to incidents

Gary Koopmann Graylog feline reporter.

Use Graylog pipelines to enrich your logs and make them easier to read.
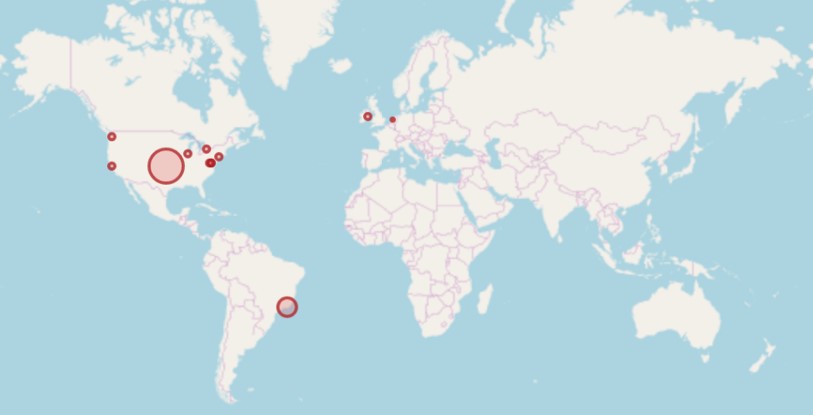
Having additional data on logs that contain IP addresses that gives you their Geolocation helps in your investigations and understanding of your traffic patterns. Here’s a guide to set up Graylog and enrich your data with this info.

Gary Koopmann intrepid feline reporter for Graylog.
Centralized log management brings valuable information to one place. See how Graylog helps you use historical data to get more concrete insights.

There are several standardized log formats that are most commonly generated by a wide assortment of different devices and systems. It is important to understand how they operate and differ from one another.
Follow Us:
© 2024 Graylog, Inc. All rights reserved